What Network and Security Engineers are expected to know?
It is an exciting but often overwhelming time to enter the networking and security field. The line between “infrastructure” and “code” is blurring, and the expectations for junior engineers are shifting from knowing how to click buttons to understanding how systems communicate.
Here is my view on a focused guide to what you should prioritise, the trends you can’t ignore, and how to develop a troubleshooting mindset.
1. The Core Fundamentals (The “Non-Negotiables”)
Before chasing the latest buzzwords, you must have a “deep-tissue” understanding of how data actually moves.
- The OSI Model & TCP/IP: Don’t just memorise the layers; understand how a packet is encapsulated and de-encapsulated as it moves from a laptop to a server(this may be on the internet, in an intranet, or in a private cloud).
- Subnetting & Routing: You should be able to calculate subnets in your head (or very quickly on paper) and understand the difference between OSPF (internal) and BGP (the language of the internet). – also have knowledge of EIGRP/ISIS.
- DNS & DHCP: These are the “heartbeat” services. If these fail, the network is “down” to the user.
- Basic Linux: The world’s networking gear and security tools run on Linux. You need to be comfortable with the CLI, file permissions, and
grep.
2. The Modern Tech Stack
As a junior Network and Security Engineer, you aren’t expected to be an architect, but you should be “dangerous” in these three areas:
Network Infrastructure
- Campus LAN Architecture (Core, Distribution, Access Switches).
- SD-WAN: Traditional hardware-centric networking is moving toward software-defined models.
- Wireless Fundamentals: Understand WPA3, Wi-Fi 6E, and how RF interference works.
- Datacenter – VXLAN, EVPN, Multi-site and Multi PoD.
Security Essentials
- Zero Trust Architecture: The old “perimeter” (firewall) is dying. Learn the philosophy of “Never Trust, Always Verify.”
- Identity & Access Management (IAM): Learn how SAML, OAuth, and MFA work. Identity is the new firewall.
- Firewalls (NGFW): Know how to configure policies, but more importantly, understand SSL Decryption, Remote Access VPN, Site to Site VPN and NAT.
- Load Balancers – Web Application Firewall
Automation & Cloud
- Python/Ansible: If you have to do a task three times, script it. Learn how to use APIs to pull data from a Network Devices.
- Cloud Basics: Get a fundamental cert in AWS, Azure, or GCP. Networking in the cloud (VPCs, Security Groups) is vastly different from on-premise.
3. The “Engineer’s Mindset”: Troubleshooting
The difference between a technician and an engineer is how they handle a crisis. Here is the approach I recommend:
- The Bottom-Up Approach: Always check Layer 1 first. Is it plugged in? Is the link light on? You’d be surprised how many “complex” issues are just bad cables.
- Check Logs: Always check the Device Logs (which give any indication of an issue to guide you).
- Isolate the Scope: Ask: “Who is affected? When did it start? What changed?” If only one user is down, it’s a workstation issue. If everyone is down, it’s a gateway issue or a device in the path is faulty (e.g., failed or in failover).
- Reproduce the Issue: If you can’t make the error happen on command, you can’t prove you’ve fixed it.
- Use Your Tools: Get comfortable with
ping,traceroute,nslookup, and especially Wireshark. Packets don’t lie; they tell the true story of what is happening on the wire. - Use AI, but it is not a 100% solution; it improves skills by understanding syntax.
4. Trends to Watch
To stay relevant over the next 5 years, keep an eye on these:
- AI-Ops: Using Artificial Intelligence to predict network failures before they happen.
- SASE (Secure Access Service Edge): The convergence of WAN and Security into a single cloud-delivered service.
- Post-Quantum Cryptography: How we will secure data once quantum computers can break current encryption.
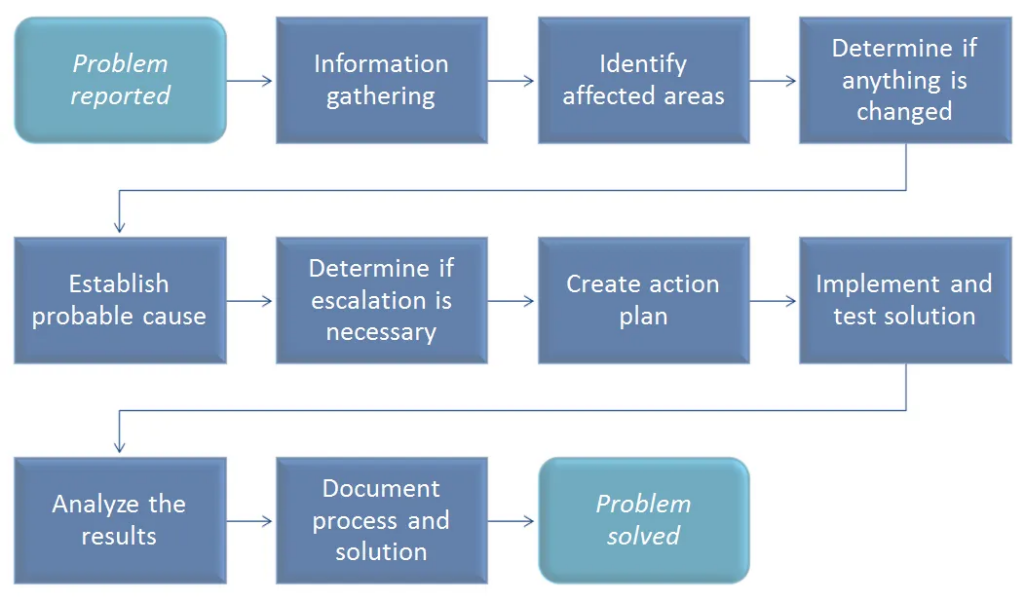
Incident Solving Flows :
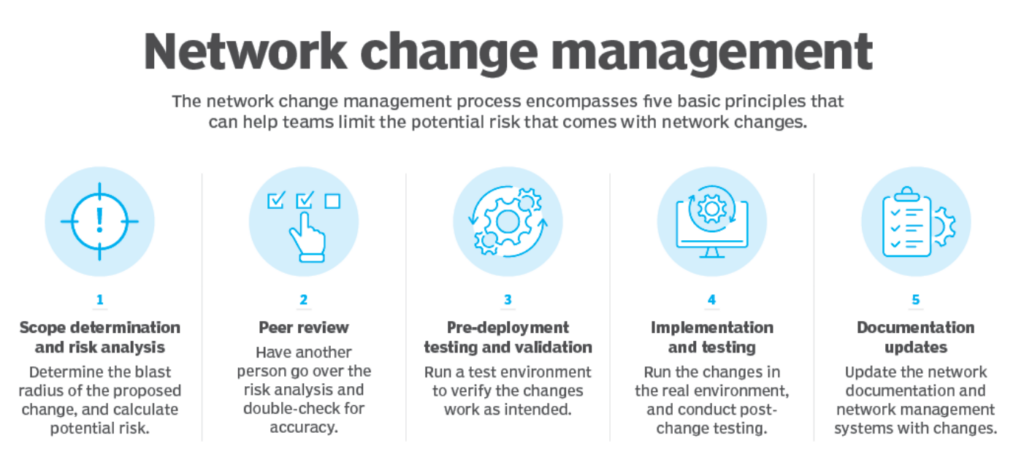
Change Management Flow :
Final Thought: Stay Curious
The most successful engineers I’ve worked with aren’t necessarily the ones with the highest IQ—they are the ones who are relentlessly curious. When something breaks, and you fix it, don’t just walk away. Spend 10 minutes figuring out why the fix worked(Document it and share it so other Learns can follow the same practice).
One of the dangerous environments is Silo Engineer (they do not communicate, they make changes without proper communication or follow the process, they do not want to document, because they are not sure about the solution they are fixing or deploying, and they will be hidden in the space and wait for the problem to occur again, and wait for someone will fix it.
Always discuss widely and openly, right or wrong, take input from experienced engineers who have worked on it before, improve it based on their feedback, and share the improvement with the team (this is a cycle of improvements).
Tip: Build a home lab. Whether it’s physical old Cisco/other vendor gear or virtual tools like CML, PNET, or Container Lab, having a place to break things without getting fired is the fastest way to learn.

Happy Labingggggggggggggggggggg !