Modernizing Enterprise Connectivity: The Evolution to Unified Cloud-Edge Security
The traditional network perimeter has dissolved. As organizations shift toward a “work from anywhere” model and migrate critical workloads to the public cloud, the rigid, data-center-centric architectures of the past are becoming bottlenecks. To stay agile and secure, enterprises are adopting a converged framework that integrates networking and security into a single, cloud-native stack.
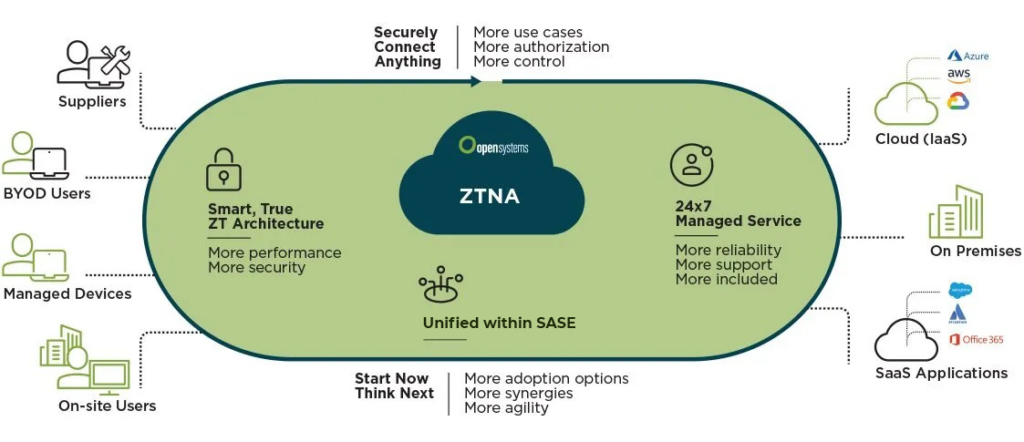
The Converged Architecture: Networking and Security Synergy
The true power of this modern approach lies in the marriage of intelligent routing with identity-centric security. By unifying these functions, businesses can ensure that connectivity is not only fast but intrinsically secure at every point of presence (PoP).
1. Agile Connectivity Layer (Formerly Networking Services)
The foundation of a unified cloud-edge platform is built on a resilient, high-performance global backbone.
- Intelligent Path Optimization: Utilizing software-defined wide area networking to dynamically route traffic based on real-time application requirements and circuit health.
- Global Transit Backbone: A private, low-latency core that connects edge locations worldwide, bypassing the unpredictability of the public internet.
- Distributed Edge Presence: Strategic points of presence (PoPs) that bring processing power closer to the end user, minimizing latency and maximizing performance.
2. Identity-Centric Defense Stack (Formerly Security Services)
Security is no longer a “bolt-on” feature; it is baked into the connection itself through an identity-driven model.
- Granular Perimeter-less Access (ZTNA): Implementing the principle of “never trust, always verify” by granting access based on the user’s specific identity and context rather than their location.
- Advanced Web Filtering & Threat Protection (SWG): Protecting users from malicious domains and sophisticated web-borne threats through continuous URL inspection and malware scanning.
- Shadow IT & Data Governance (CASB): Gaining deep visibility into SaaS usage and enforcing data loss prevention (DLP) policies across cloud-based applications.
- Unified Cloud Firewall (FWaaS): Deploying a robust, scalable firewall in the cloud that provides consistent protection across all branches and remote users.
The Core Pillars of a Unified Cloud-Edge Platform
To be effective, this architecture must be built on five fundamental design principles:
- Identity-First Verification: Access is determined by who the user is, not where they are.
- Native Cloud Delivery: The entire stack is built to scale elastically within a global cloud environment.
- Active Threat Mitigation: Real-time analysis ensures that protection is proactive rather than reactive.
- Policy-Driven Orchestration: Centralized control allows for uniform security rules across the entire global footprint.
- Implicit Zero Trust: Every connection is treated as potentially hostile until authenticated and authorized.
Operational Advantages
Transitioning to a converged cloud-edge model yields significant business benefits:
- Infrastructure Consolidation: Removing the need for disparate point products reduces administrative overhead and complexity.
- Hardened Security Posture: A unified policy engine ensures there are no “blind spots” in the security stack.
- Optimized End-User Experience: Users receive consistent, high-speed access to resources, whether they are in a branch office or a coffee shop.
- Total Cost of Ownership (TCO) Reduction: Moving to a subscription-based cloud model eliminates heavy capital expenditures on on-premises hardware.
ZTNA Implementation: A Technical Deep Dive
Implementing Zero Trust Network Access (ZTNA) effectively requires moving beyond a simple “VPN replacement” mindset to a multi-layered security strategy focused on five key pillars: identity, devices, networks, applications, and data.
Core Implementation Phases
- Phase 1: Hybrid VPN Migration
Initially, map private application usage and set access levels mirroring your current VPN. This ensures user productivity remains stable during the transition. - Phase 2: Granular Microsegmentation
Create specific access policies for high-value resources, such as infrastructure servers and management ports, to prevent lateral movement. - Phase 3: Context-Aware Expansion
Roll out ZTNA to all users (remote and on-site), routing all requests through encrypted microtunnels that validate identity, device health, and real-time context before granting access.
Top SASE & ZTNA Solutions
The market is currently led by “pure-play” cloud security vendors and established networking giants, each with distinct advantages based on your existing infrastructure.
| Vendor | Solution Name | Best For… | Key Strength [Source] |
|---|---|---|---|
| Zscaler | Private Access (ZPA) | Enterprise-scale cloud-native security | Largest global security cloud; unified agent for ZTNA and web gateway. |
| Palo Alto Networks | Prisma Access | Hybrid environments & security operations | Seamless integration with existing NGFW and Cortex XDR/XSIAM for a unified “security brain”. |
| Cisco | Secure Access / Duo | Cisco-centric estates | Strongest identity-first focus; deep integration with ISE and Duo for hybrid ZTNA/VPN. |
| Cloudflare | Cloudflare One | Performance & low-latency | Uses a massive globally distributed edge network to deliver a fast “VPN-off” user experience. |
| Netskope | Intelligent SSE | Data-centric security | Exceptional DLP and CASB capabilities for organizations prioritizing sensitive data protection. |
Deployment Model Comparison
Choosing the right model depends on your data residency needs and where your applications live.
- Cloud-Based (SaaS): Ideal for cloud-first organizations. It offers minimal deployment effort and high scalability but requires usage monitoring to manage “pay-as-you-go” costs.
- On-Premises: Best for highly regulated industries (e.g., finance, healthcare) with strict data residency requirements. It provides maximum control but requires more setup and hardware maintenance.
- Universal/Hybrid: The most flexible option for enterprises with mixed workloads. It allows critical workloads to stay on-site for performance/compliance while leveraging the cloud for remote user scaling.
Happy Labingggggggggggggggg!