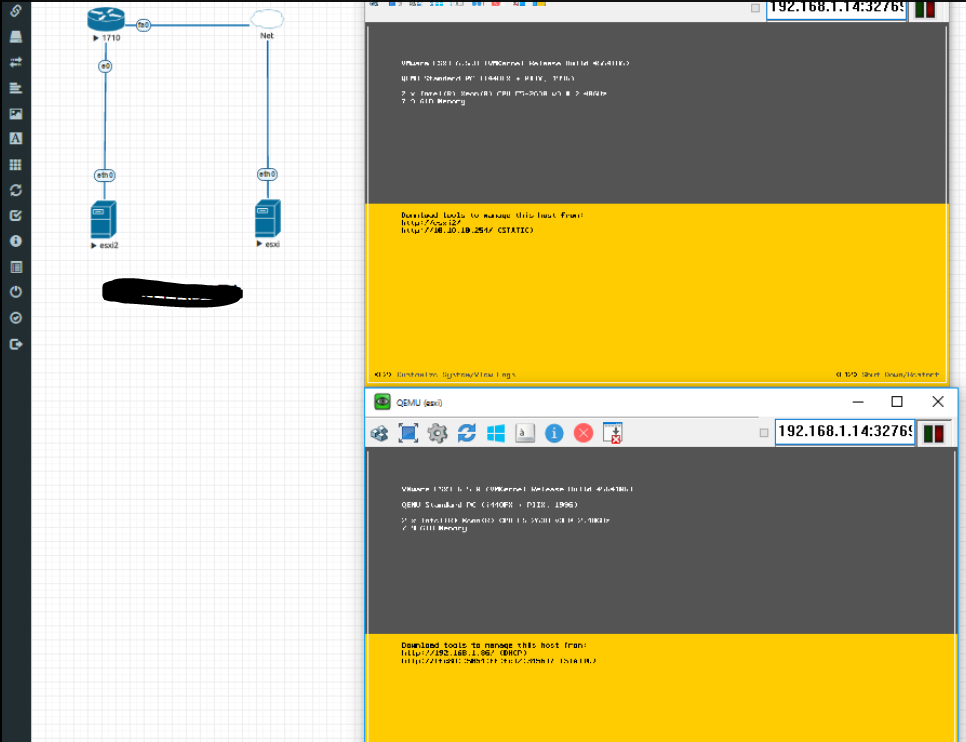
Installing Esxi inside EVE-NG to test 2 x Esxi for LAB
Installing Esxi inside EVE-NG to test 2 x Esxi for LAB
Just been testing long time, how i can i deploy 2 esxi inside EVE-Ng to test my lab.
Struggled lot and spend enough time in Vmware forum and Qemu site to explore and fix the issue.
I found the issue is most of the EVE-NG does not expose the CPU information to esxi
Since EVE-NG already virtual machine and i am trying another nested vm inside EVE-NG
Finally i could able to achieve, i will write the steps how you can create own lab if Esxi inside EVE-NG full step later. after through testings.