IP Device Tracking (IPDT)
For a long time, as I recall, the IPDT has been available, introduced in iOS 15 and later versions. (but some limitations). I was not much used to it since we use the CLI command most of the time, the famous one :
show mac-address table or show ip arp to view most of the information.
However, I recently started using IPDT in an environment where SD-Access deployment is being used with Cat 9300 Switches and IOS XE 17.x code. IPDT helps me simplify traditional commands into a new, modern way to view and track the device.
Cisco IP Device Tracking (IPDT) is a fundamental network security feature that maintains a dynamic database of IP-to-MAC address bindings for devices connected to Cisco switches. This feature serves as the backbone for numerous security and network management functions, including 802.1X authentication, MAC Authentication Bypass (MAB), TrustSec, and Identity Services Engine (ISE) integration.
IPDT operates by leveraging ARP snooping and DHCP snooping to automatically discover and track network devices, creating a comprehensive mapping of device locations within the network infrastructure. The feature has evolved from basic IP tracking to a sophisticated framework called Switch Integrated Security Features (SISF), which provides enhanced capabilities for both IPv4 and IPv6 environments
High level Information :
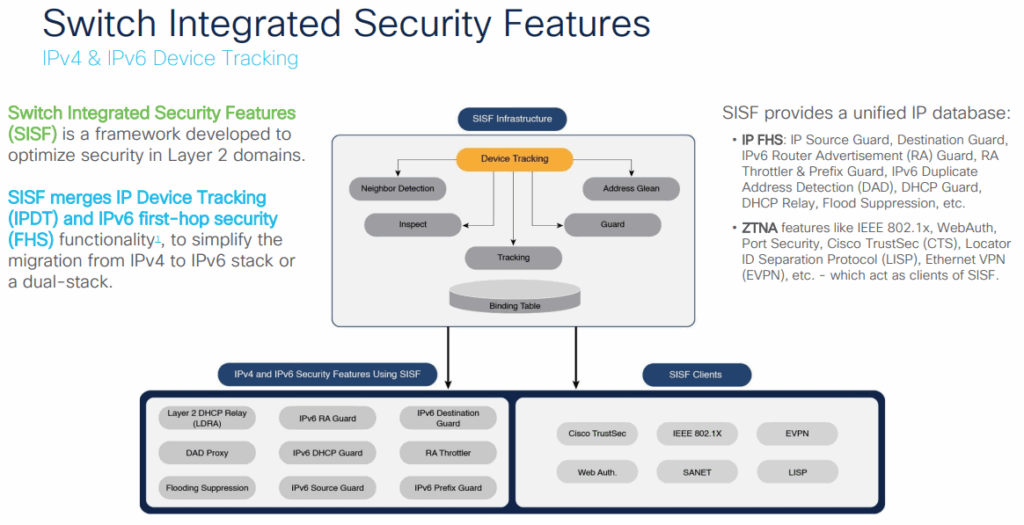
Technical Architecture and Operation
Core Components
IPDT consists of several key components that work together to provide comprehensive device tracking capabilities:
ARP Snooping Module: Monitors ARP packets to learn IP-to-MAC bindings and detect new devices on the network. This component intercepts ARP requests and replies to populate the binding database.
DHCP Snooping Integration: Works in conjunction with DHCP snooping to detect IP address assignments and revocations. When DHCP snooping is enabled, IPDT automatically learns about new device IP assignments.
Binding Table Database: Maintains a centralized database of IP-to-MAC-to-port bindings for all tracked devices. This database serves as the authoritative source for device location information.
Probe Mechanism: Sends periodic ARP probes to validate device presence and maintain accurate binding information. By default, probes are sent every 30 seconds using a sender IP address of 0.0.0.0.
Operational Workflow
The IPDT operational workflow follows these key steps:
- Device Detection: When a new device connects to the network, IPDT detects it through ARP requests/replies or DHCP transactions
- Binding Creation: The system creates an entry in the binding table containing the device’s IP address, MAC address, interface, and VLAN information
- Periodic Validation: IPDT sends ARP probes to validate device presence and maintain binding accuracy
- Table Maintenance: The system automatically updates or removes entries based on device activity and probe responses
- Integration Services: Binding information is shared with dependent features like 802.1X, TrustSec, and ISE for security policy enforcement
Advanced Features and Capabilities
Delayless IPDT
Modern Cisco switches support Delayless IPDT, which significantly improves ARP packet processing performance1. This feature allows original ARP traffic to be forwarded through hardware while only sending copies to the CPU for binding table updates, reducing ARP delivery delays.
Key Benefits:
- Hardware-accelerated ARP forwarding
- Reduced CPU overhead
- Improved network performance
- Maintains full tracking capabilities
Limitations:
- Does not work with Dynamic ARP Inspection (DAI) enabled
- Automatically enabled when IPDT policies are configured
- Cannot be manually controlled per interface
SISF-based Device Tracking
The evolution of IPDT led to Switch Integrated Security Features (SISF), which provides enhanced capabilities:
Enhanced Features:
- Policy-based configuration management
- Full IPv4 and IPv6 support
- Centralized binding table
- Advanced security enforcement options
- Integration with first-hop security features
Migration Path: Organizations using legacy IPDT commands should migrate to SISF-based device tracking for optimal performance and future compatibility.
Configuration and Implementation
Basic Configuration Commands
| Command | Purpose | Context |
|---|---|---|
device-tracking policy <policy-name> | Creates a custom device tracking policy | Global configuration |
device-tracking attach-policy <policy-name> | Attaches policy to interface/VLAN | Interface/VLAN configuration |
device-tracking | Enables default device tracking | Interface/VLAN configuration |
limit address-count <count> | Sets maximum addresses to track | Policy configuration |
security-level glean | Enables learning without enforcement | Policy configuration |
security-level guard | Enables learning with enforcement | Policy configuration |
Monitoring and Troubleshooting Commands
| Command | Purpose | Context |
|---|---|---|
show device-tracking database | Displays the device tracking database | Privileged EXEC |
show device-tracking policy | Shows policy configuration and targets | Privileged EXEC |
show ip device tracking all | Displays all IPDT information | Privileged EXEC |
show ip device tracking interface <interface> | Shows IPDT status for specific interface | Privileged EXEC |
debug device-tracking | Enables debugging for device tracking | Privileged EXEC |
Advantages and Benefits
Network Security Enhancement
IPDT provides significant security benefits by enabling advanced network access control mechanisms:
Identity-Based Access Control: Supports 802.1X authentication and MAB by providing device IP information to RADIUS servers. This enables policy enforcement based on device identity and location.
TrustSec Integration: Facilitates Cisco TrustSec policy enforcement by maintaining accurate device-to-port mappings. This enables security group tag (SGT) assignment and policy enforcement.
Dynamic ACL Population: Enables dynamic access control list updates based on device location and identity. This provides granular security control without manual configuration.
Operational Advantages
Network Visibility: Provides comprehensive device tracking without requiring routing capabilities on access switches. This enables better network monitoring and troubleshooting.
Automated Device Discovery: Automatically detects and tracks new devices as they connect to the network. This reduces manual inventory management overhead.
Multi-Protocol Support: Supports both IPv4 and IPv6 device tracking in modern implementations. This ensures compatibility with dual-stack environments.
Integration Capabilities: Seamlessly integrates with multiple Cisco security features and third-party solutions. This provides a unified security framework.
Best Practices and Recommendations
Implementation Guidelines
Assessment Phase: Evaluate existing network infrastructure and identify devices that may be sensitive to ARP probes. Pay particular attention to industrial control systems and legacy equipment.
Gradual Deployment: Implement IPDT gradually across the network, starting with non-critical segments. Monitor for any unexpected behavior or device failures.
Policy Design: Design SISF policies that align with security requirements while minimizing operational impact. Consider different policies for different device types and network segments.
Integration Planning: Plan integration with existing security infrastructure including ISE, and other NAC solutions. Ensure proper RADIUS attribute configuration for device tracking information.
Monitoring and Maintenance
Regular Monitoring: Implement regular monitoring of device tracking databases and probe activity. Use show commands to verify proper operation and identify potential issues.
Performance Optimization: Optimize probe intervals and timeouts based on network requirements. Consider using Delayless IPDT where available to improve performance.
Troubleshooting Procedures: Establish clear procedures for troubleshooting IPDT-related issues. Include steps for identifying and resolving duplicate IP conflicts and device interference.
Conclusion
Cisco IP Device Tracking represents a critical component of modern network security architecture, providing essential device visibility and enabling advanced security policy enforcement. While the technology has evolved from basic IP tracking to sophisticated SISF-based implementations, the core principle of maintaining accurate device-to-location mappings remains fundamental to network security.
Success with IPDT requires careful planning, proper configuration, and ongoing monitoring to balance security benefits with operational requirements. Organizations must consider the specific characteristics of their network environment, particularly regarding industrial equipment and legacy systems, when implementing device tracking solutions.
The evolution toward SISF-based device tracking provides enhanced capabilities and improved performance, making it the recommended approach for new deployments and existing infrastructure upgrades. By following best practices and maintaining awareness of known limitations, organizations can leverage IPDT to significantly enhance their network security posture while maintaining operational efficiency.
On Cat 9K Configuration example will be posted with some show commands soon. in the IPTD Part2
Happy Labbbbbbbbbbbbbbing ………………..!