88 Days to CCIE SEC v6.1 Lab
ISE Decoding MAC Authentication Bypass (MAB)
In the real world, your network is haunted by “dumb” devices—printers, IP cameras, and building controllers—that can’t perform 802.1X. For these, we use MAC Authentication Bypass (MAB).
What is MAB?
MAB is a fallback mechanism that uses the device’s MAC address as both the username and the password. It is considered “weak” authentication because MAC addresses are easily spoofed, but it is essential for operational continuity.
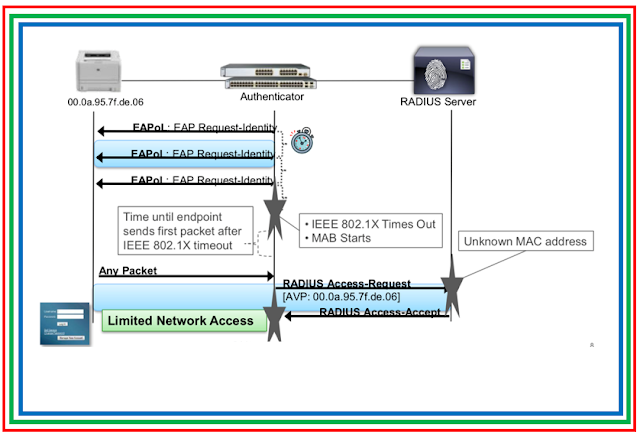
How MAB “Tricks” the Switch
MAB doesn’t start immediately. By default, a Cisco switchport prefers 802.1X. Here is the step-by-step flow:
- Initial EAPOL Exchange: The switch sends EAP-Request/Identity frames. The “dumb” device ignores them because it doesn’t speak EAP.
- The Timeout: The switch waits for a response (governed by the
dot1x timeout tx-periodanddot1x max-reauth-reqtimers). - The Switch to MAB: Once the 802.1X attempts fail, the switch “bypasses” 802.1X and creates a RADIUS Access-Request.
- User-Name (Attribute 1): The MAC address (e.g.,
001122334455). - User-Password (Attribute 2): The MAC address.
- Service-Type (Attribute 6): Set to
10(Call Check), signaling to ISE that this is a MAB request.
- User-Name (Attribute 1): The MAC address (e.g.,
- ISE Processing: ISE looks up the MAC address in its Internal Endpoints database or an external identity store.
- Authorization: If found, ISE returns an Access-Accept with the appropriate VLAN or dACL.
Use Case: The Printer Problem
Scenario: A hospital has 500 legacy printers that don’t support certificates. They need to be on a specific VLAN and restricted from accessing the Internet.
- The Solution: Use ISE Profiling with MAB.
- The Logic: Instead of just checking if the MAC exists, ISE uses Device Profiling (DHCP snooping or HTTP user-agents) to verify the device is actually a printer and not a laptop spoofing a printer’s MAC.
- The Result: If the device “looks and acts” like a HP LaserJet, ISE pushes a dACL allowing it to talk only to the Print Server.
Performance Tuning
In a standard config, a MAB device might wait 30+ seconds to get network access while 802.1X times out. To fix this in production, we use Cisco Common Classification Policy Language (C3PL) to trigger MAB and 802.1X simultaneously or shorten timers:
! Shorten the gap for MAB devices
interface GigabitEthernet1/0/1
authentication order dot1x mab
authentication priority dot1x mab
mab
dot1x timeout tx-period 7 # Reduce from default 30s
The “Security vs. Usability” Trade-off
| Feature | 802.1X | MAB |
|---|---|---|
| Identity Basis | Certificates/Credentials | Hardware MAC Address |
| Security Level | High (Encrypted) | Low (Spoofable) |
| Management | Supplicant Required | Agentless |
Critical Action for Administrators
Always combine MAB with ISE Profiling. This adds a layer of “behavioral” security—if a “Printer” suddenly starts trying to SSH into a Core Switch, ISE can issue a Change of Authorization (CoA) to kill the port. Check out the Cisco ISE Profiling Design Guide for deep-dive logic.
Happy Labinggggggggggggggggggg!