Site to Site VPN Phase2 issue Between Fortinet and Checkpoint R80.10
I was working one of the site to site VPN config.
Most cases Checkpoint have some teethering issue with other vendor when we deploy VPN between CP and otehr vendors.
I have come across some of this issue – in common practice Checkpoint side we use bunch of allowed IP’s in the encryption domain.
in this case Fortinet coming with only set of ip address in the intresting traffic x.x.x.x/15, which is not matching with Checkpoint.
Phase1 come up as expected.
Now checkpoint release ikeview tool :
Fortinet boxes are quite picky about what Proxy-IDs/subnets they will accept in an IKE Phase 2 proposal sent by a Check Point.
Steps :
Initiate debug of VPND daemon on Check Point Security Gateway from the CLI:
You need to get on to expert mode.
To enable IKE debug mode, run in Expert mode on Security Gateway:
#vpn debug ikeon
To stop IKE debugging, run in Expert mode on Security Gateway:
#vpn debug ikeoff
Note: Enabling IKE debug mode has no resource impact on the Security Gateway. Check Point recommends disabling IKE debug mode when not in use, due to hard-drive space consideration.
Logs will be stored in :
$FWDIR/log/ike.elg or $FWDIR/log/ikev2.xmll or $FWDIR/log/legacy_ikev2.xmll
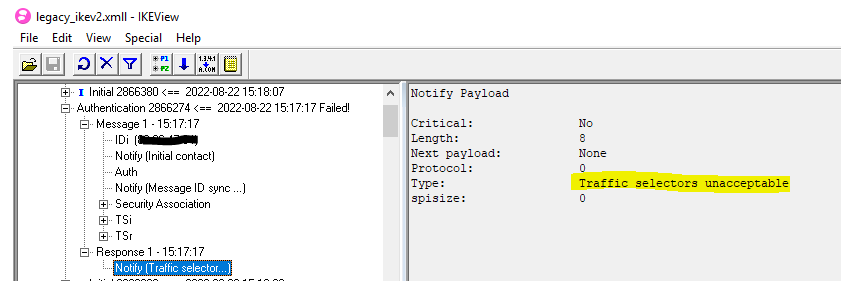
I have downloaded all 3 files locally and analysed with ikevtool.
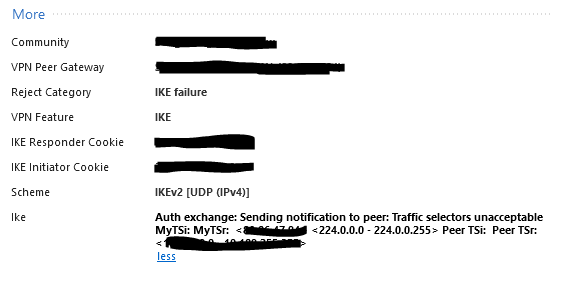
The logs show the issue as below :
before R80, we need to edit the user.def file to achieve this, but R80.10 onwards you can attached directly to VPN config specific IP address space.
Instead of broad domain, i have matched x.x.x.x/15, that fix the issue.
Phase 1 and Phase 2 comeup as expected.
Same Like cisco Forum, Checkpoint forum also very helpful to resolve the issue, and ikevtool(required permission to download) but good tool.
Happy Labbbing…!!!!