Going to CLOUD – what should we aware of ?
Going to CLOUD – what should we aware of ?
I have been hearing people, we are migrating to cloud or moving our infrastructure to cloud.
1 top question always ask customer ?
Have you understand what is cloud ?
- Most of the time i hear, they are in misconception what told by the market.
- Most of the time i hear from business we are moving to cloud to save cost – are you really saving cost – have you done some math calculation
- is your application ready for cloud ? or do you really need to go to Cloud.
My Experience is – Depends on what Business are you ? what is the key elements need to go to Cloud, what need to be really still required onsite.
Here is the some good examples, what still need to be managed by Business network and Security Engineer and Cloud provider responsibilities. ( some of them copied from Cisco Live Shamelessly)
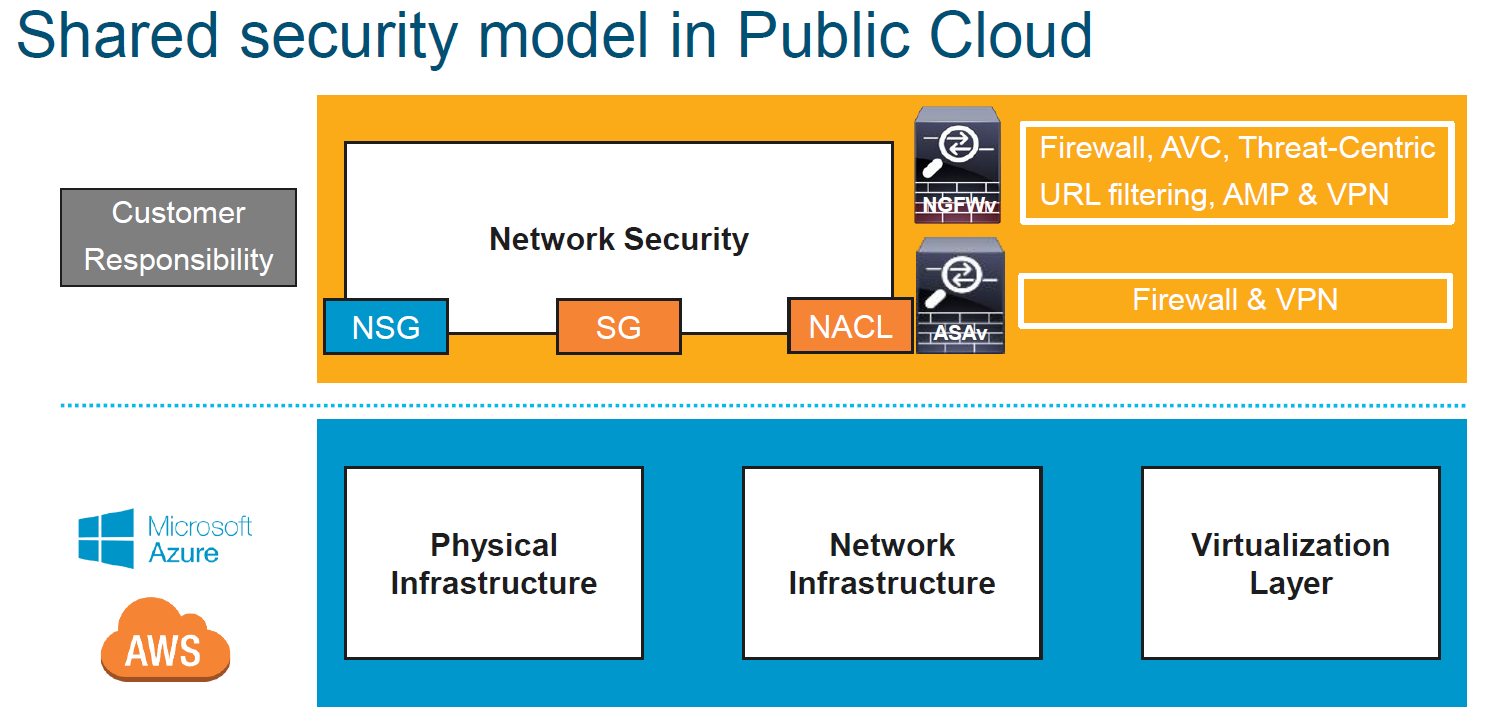
Deployment models :
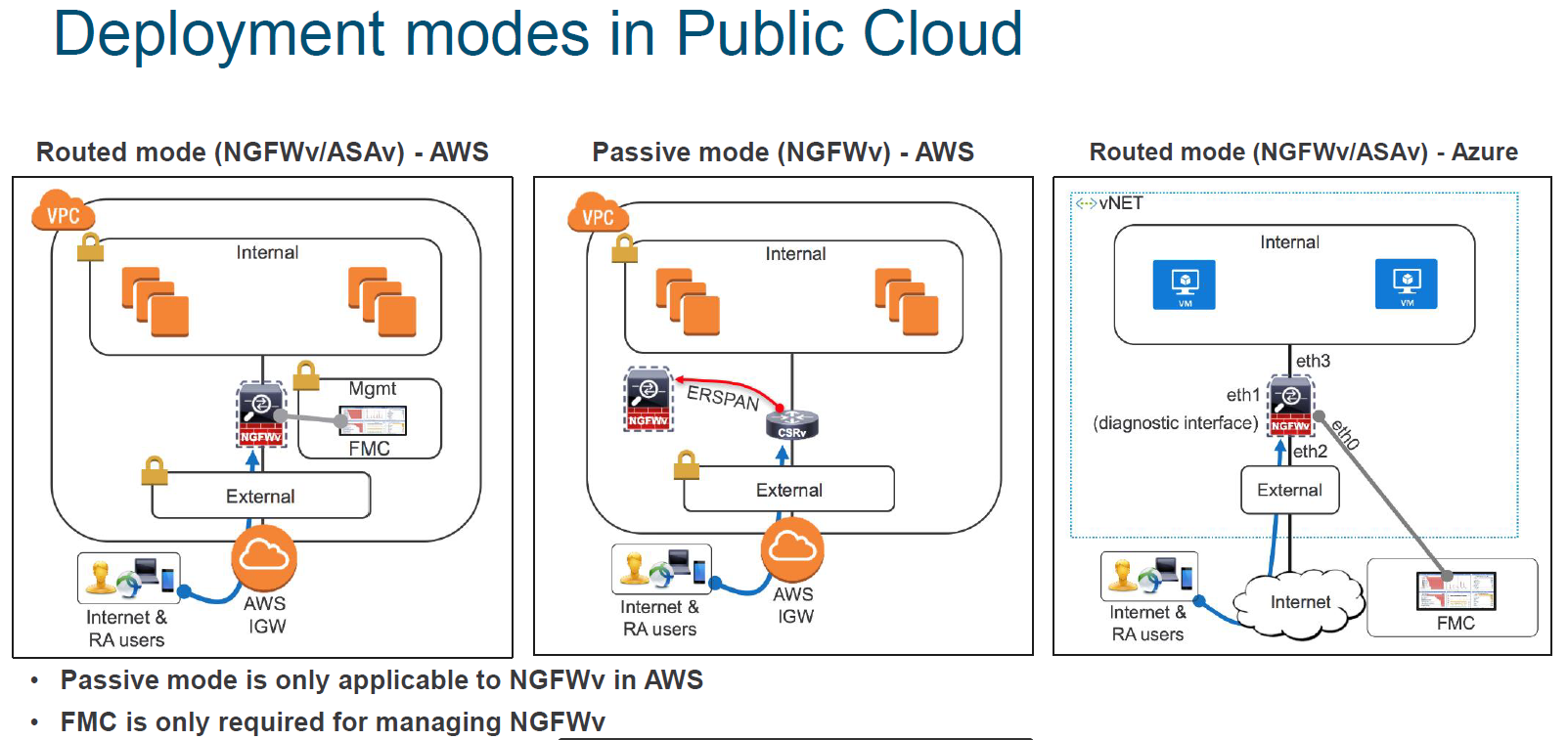
AWS :
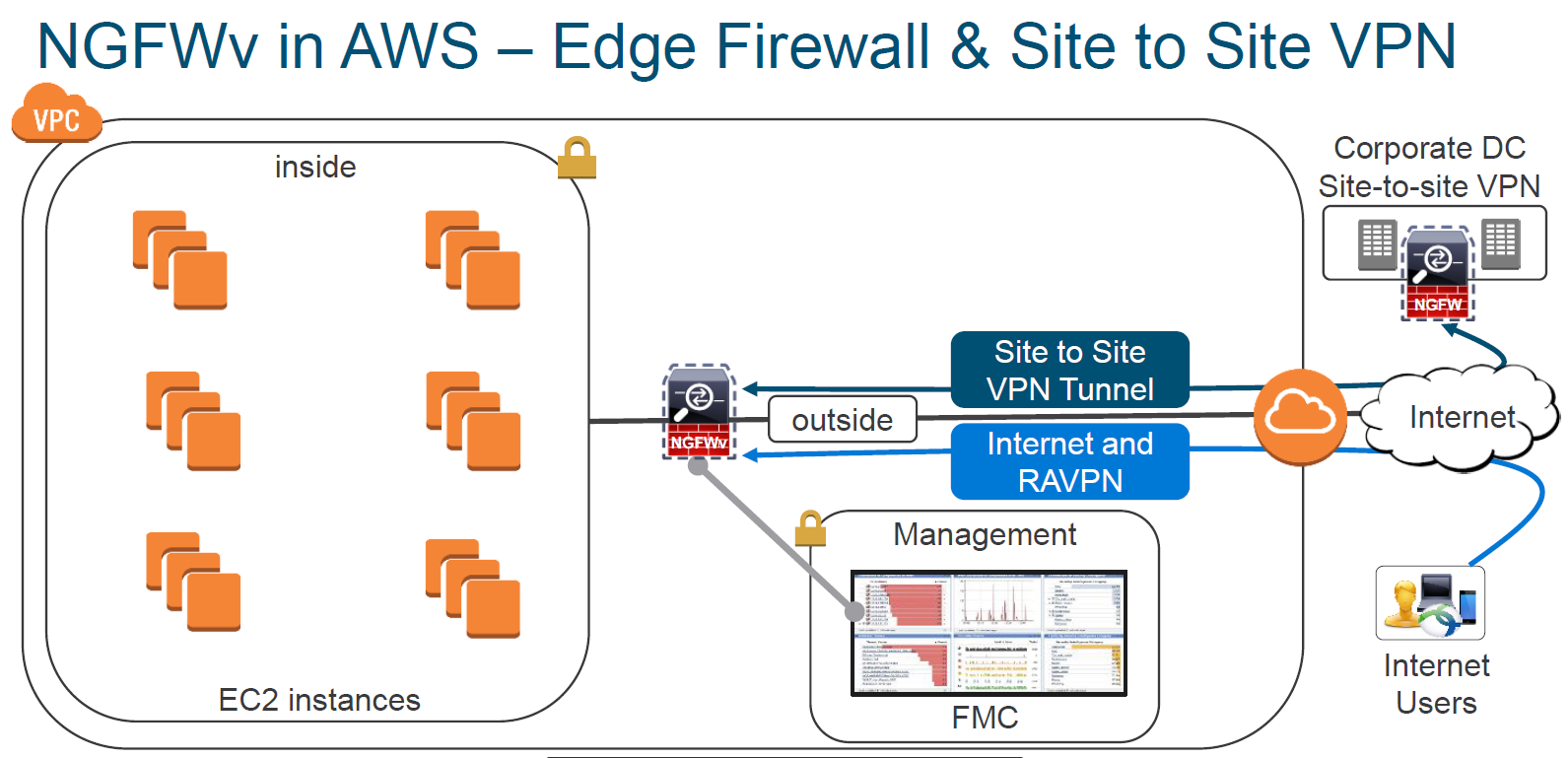
So the end is if your application / Services are not required for many to the public, always suggest having onsite DC with HA. ( it is more secure, if required DR, you have Co-location space for hosting your hardware and managed by Business IT Network and Security Team).
This is my personal experience point of view…happy Labbing ..!!!