IPsec Remote-Access VPN
IPsec Remote-Access VPN
Part of the CCIE Sec Journey created a Remote Access VPN setup.
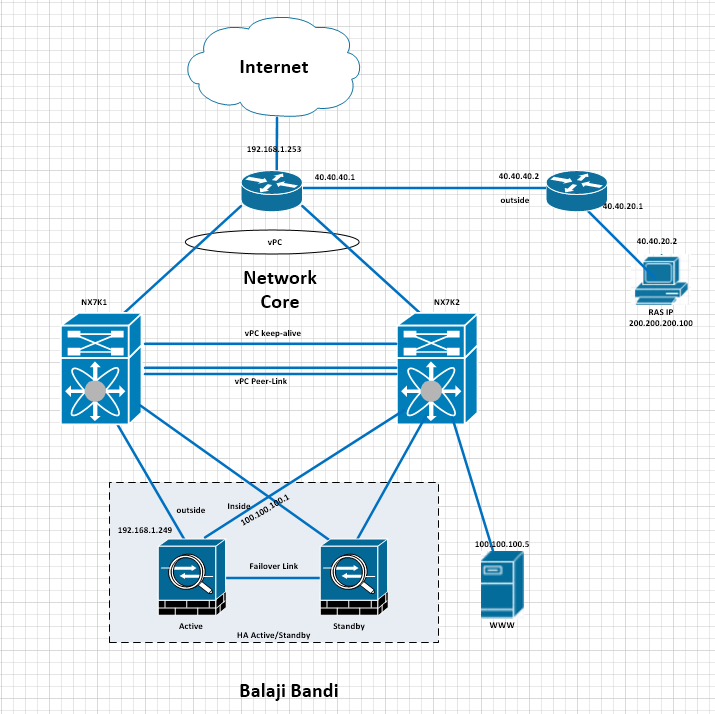
Physical Diagram for the LAB
I have used below Version of ASAv and ASDM

IP address and Physical connectivity as shown as above pictures.
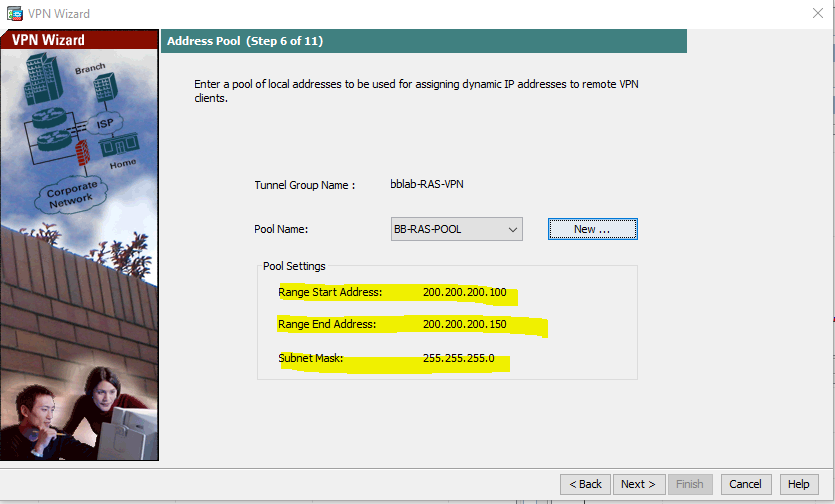
RAS pool of address 200.200.200.X /24
Before proceeding further, i expect all the devices have L3 connectivity.
Make sure Branch router / Windows PC able to ping 192.168.1.249 ( ASAv). If all devices have reachable. move to next level to configure Remove Access VPN.
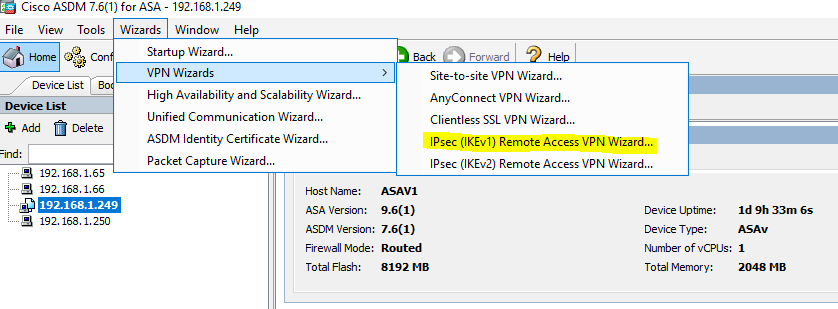
Connect to ASAv with your ASDM.
its easy to ASDM to create remove access VPN with Wizard.
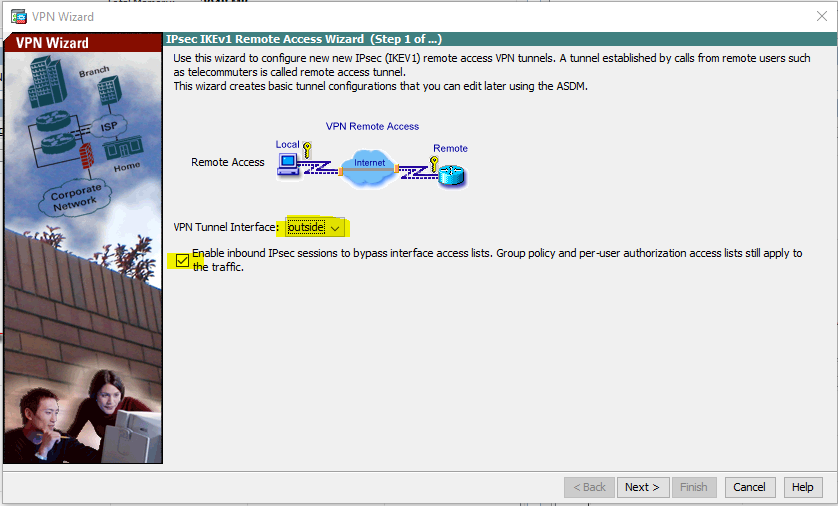
Notice the option on the screen above that is selected by default. This allows IPsec sessions to bypass access lists applied on the interface.
The default selected interface is outside, which is where we want to configure this VPN, so I will click on the Nextbutton.
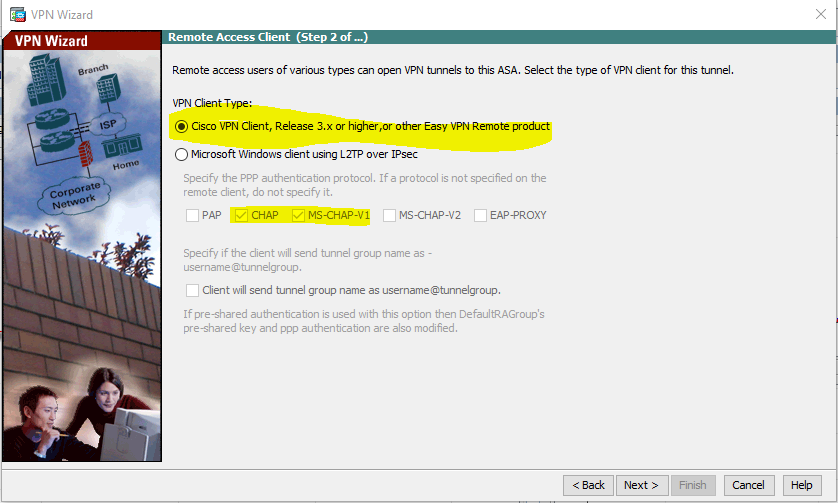
We will be using the Cisco VPN client, so I will leave the default option selected and click Next.
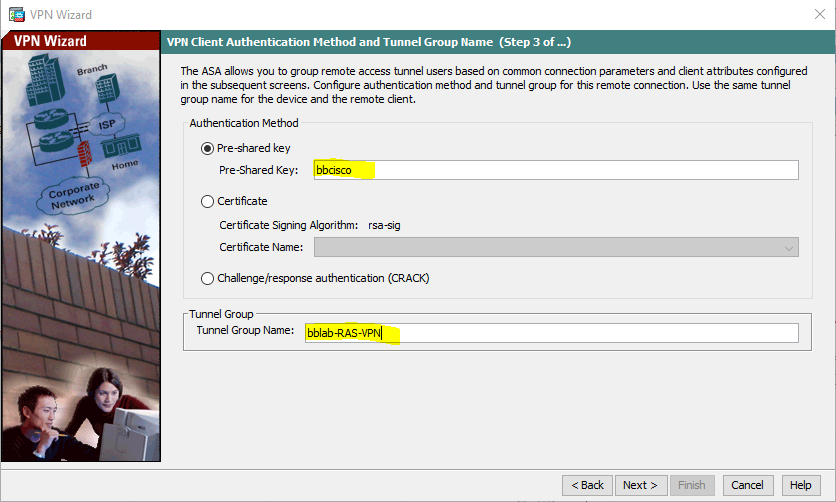
I have configured a tunnel group name of bblab-RAS-VPN and a pre-shared key of bbcisco.
(change as per your setup)
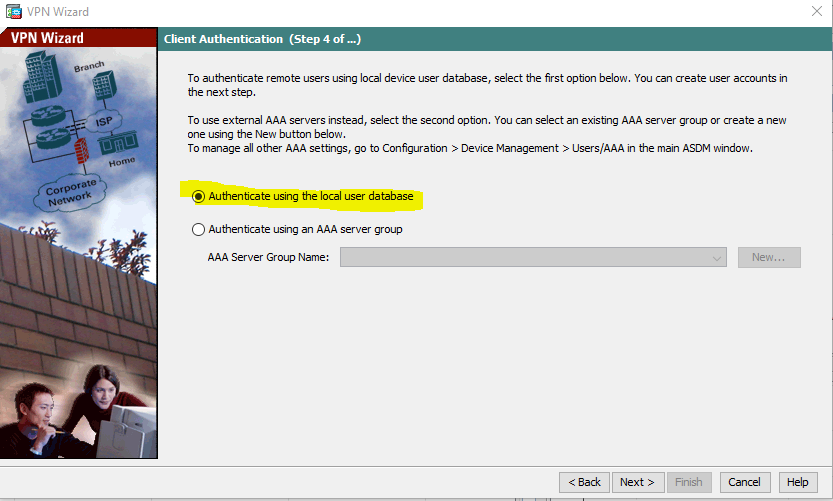
we select the method with which to authenticate the remote users. In the step before this, we configured a pre-shared key for the tunnel group.
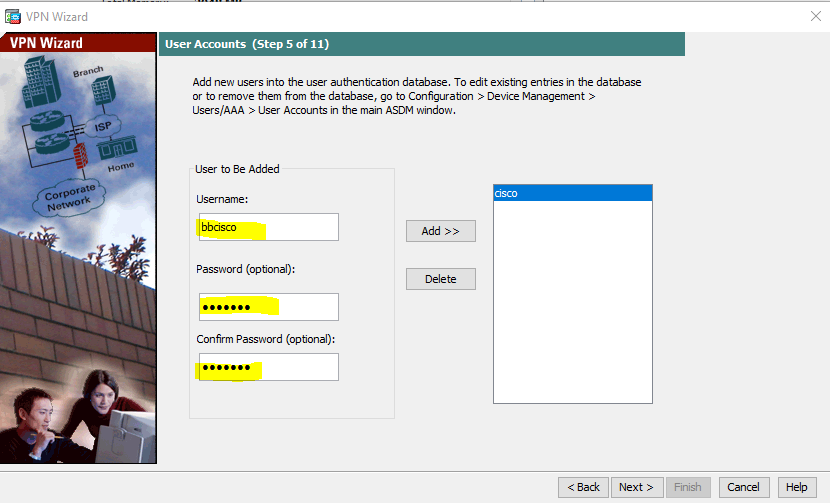
Because we specified that we want to use the local database for client authentication, the wizard prompts us to add usernames. I will add another user with username and password of bbcisco.
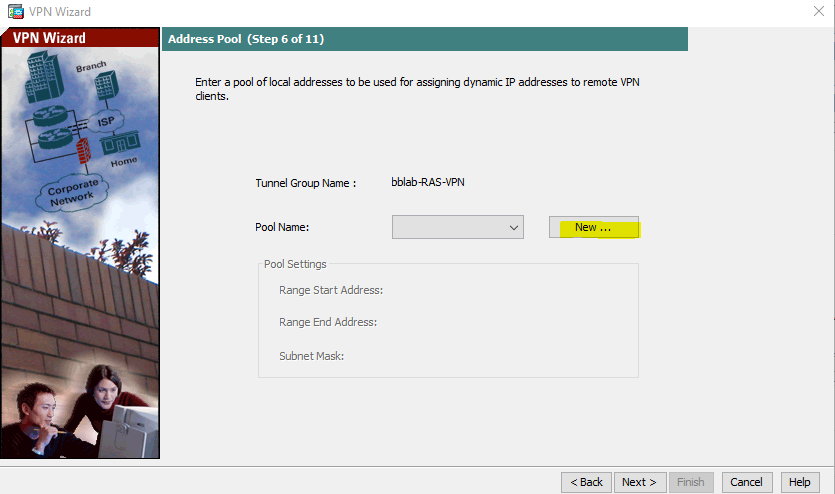
When a users connects using the VPN client, User will be assigned an IP address from an IP address pool that we configure. This is one of the reasons to have a remote access VPN, because it makes remote users become “part” of the internal network. I will click on the New button to add a local IP pool, as shown below:

I have used 200.200.200.0/24. please change the IP address range based on your setup.

DNS entry, change as per your DNS Server.
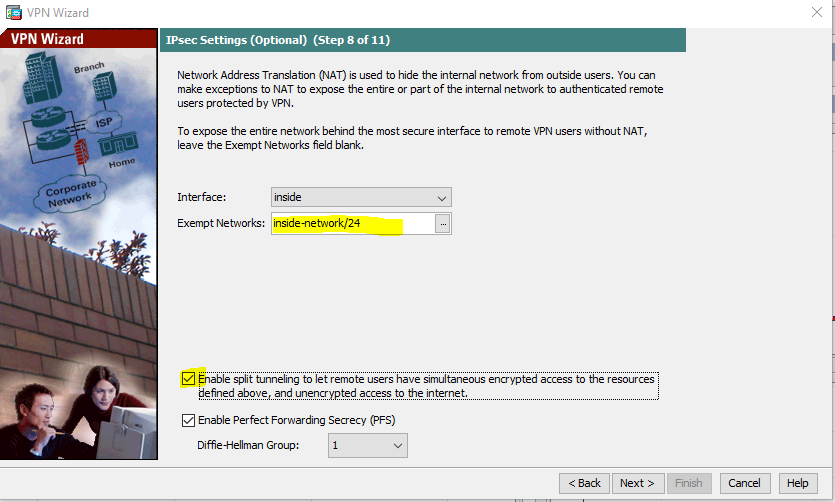
Wizard gives us the option of performing a NAT exemption so that all internal networks will be visible to remote users without any translation. Also, notice that I have selected the option to enable split tunneling. Split tunneling allows remote access VPN users to access specified networks (e.g., 100.100.100.0/24 ) through the VPN but all other traffic (e.g., Internet traffic) goes through the client’s normal gateway without going through the tunnel. If split tunneling is not enabled, even the remote access user’s Internet traffic will go through the VPN tunnel. This may be desired; it all depends on the network and your setup.
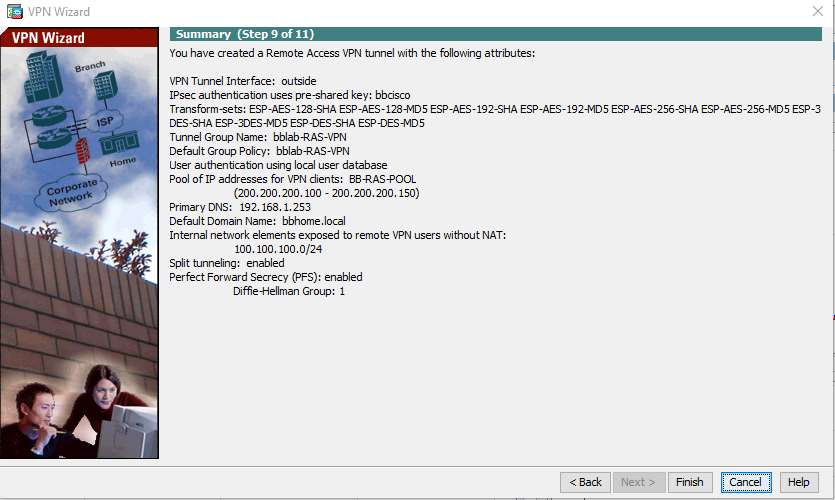
Final config. :
I have windows already installed Windows VPN Client, Now we going to configured the same.
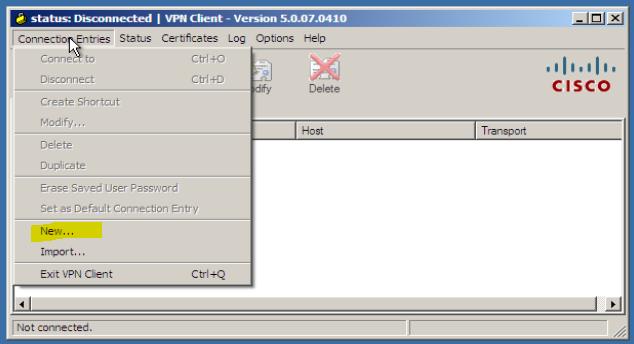
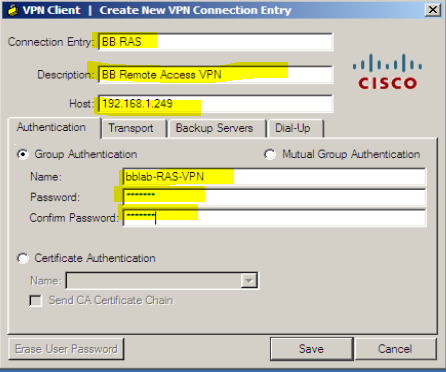
The configure we used here, before we configured in ASA, password is – bbcisco (change as per your network)
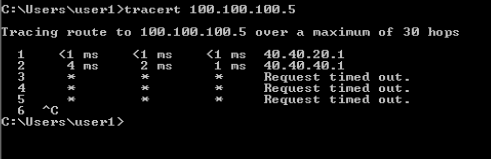
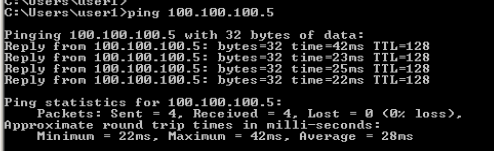
Some tests before we establish VPN. below screen shows no connection to 100.100.100.5

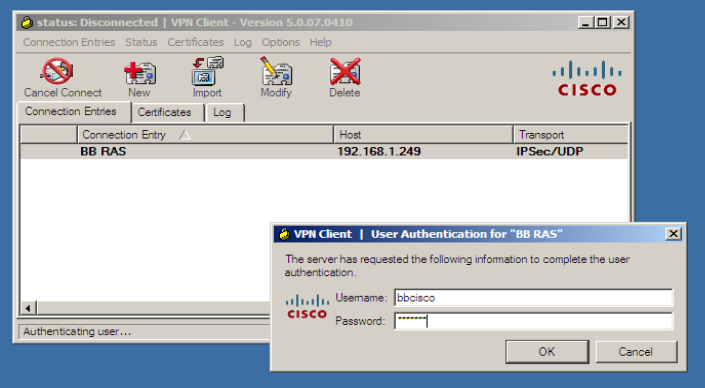
Lets connect to VPN
using
username : bbscisoc
password : passw0rd
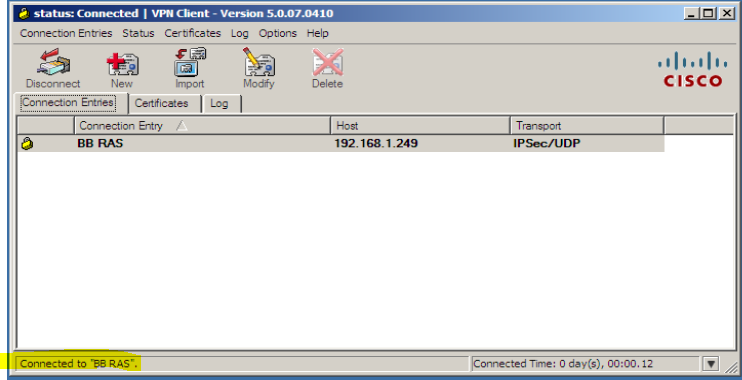
It is connected now.
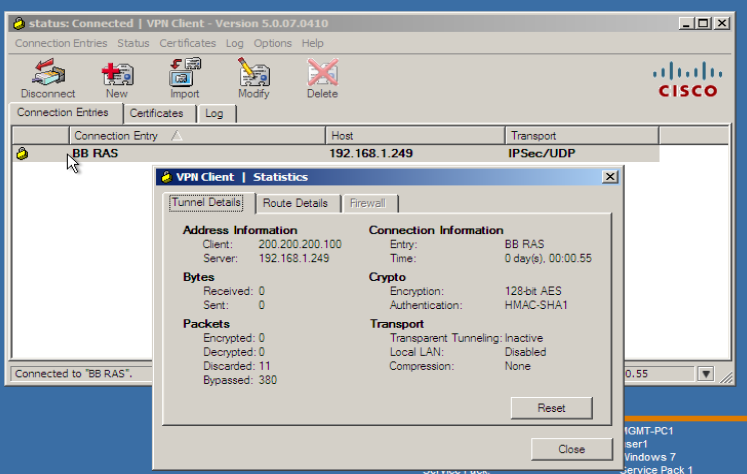
we can see some statistics.
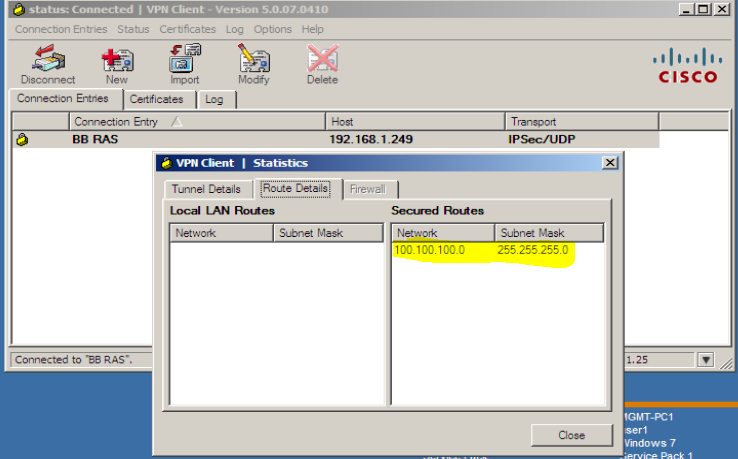
We able to access 100.100.100.0/24 network.
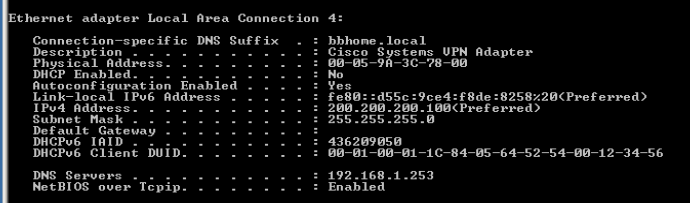
We have IP 200.200.200.100/24 as soon as we connected to remote access VPN
Some tests :
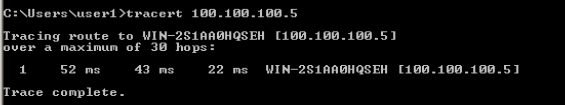
we able to ping Remote site Server, and traceroute is next hop.
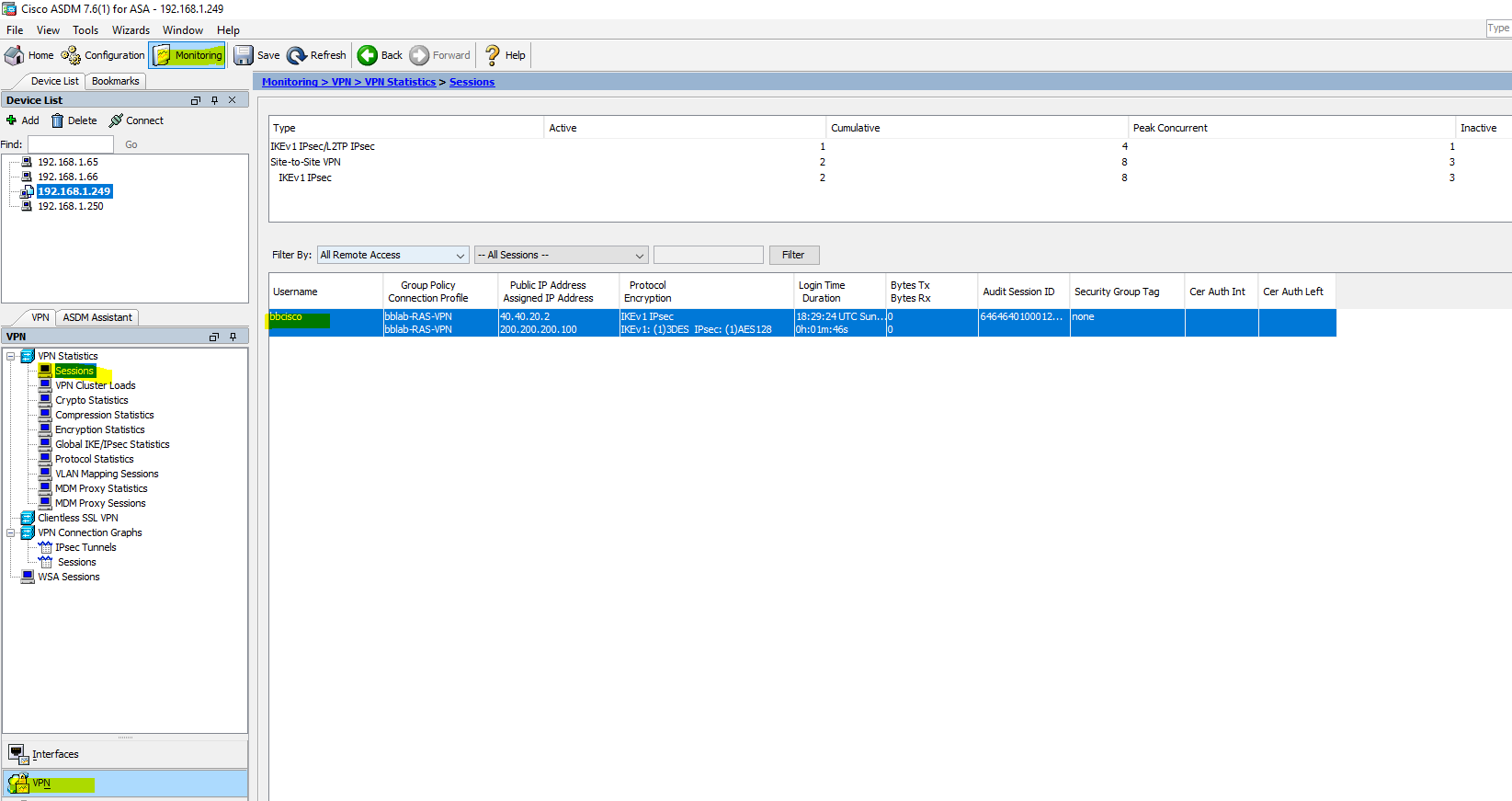
We can view Remote VPN Client connections.
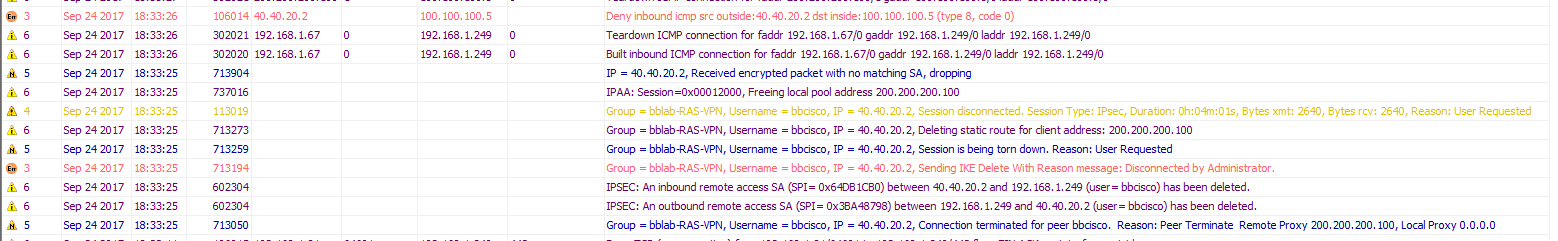
Once you terminate the connection you can see the below logs in ASDM
Happy Labiingggggggg!