ISE 2.X Learning and explore more features
As i was workiend 1.X Long Long and discontinued due that i have to working AWS cloud Service for 2-3 years for a Client.
Once I got back I had worked little time 2.2 for the short term, then moved to the organization, still Holding ACS 4.X and 5.8 ( tried many times promote ISE as demo models to protect some devices which have no control, I failed to win that confidence from the organization I work for).
I have been supporting and doing many many scenario Labs, not got a chance to write one good document, its time for ISE, since we hear marketing term from cisco now called “SD-Access” – which has major requirement of ISE , since ISE center focus interms of Scalable Groups and Identity – so refreshing my knowledege by writing this document and couple of new features to test in next blog while i am doing some Labs.
Below diagram give you one stop which tell what is ISE ( still not sure what ISE, go back to basic ISE information – may be wrong blog for newbies)
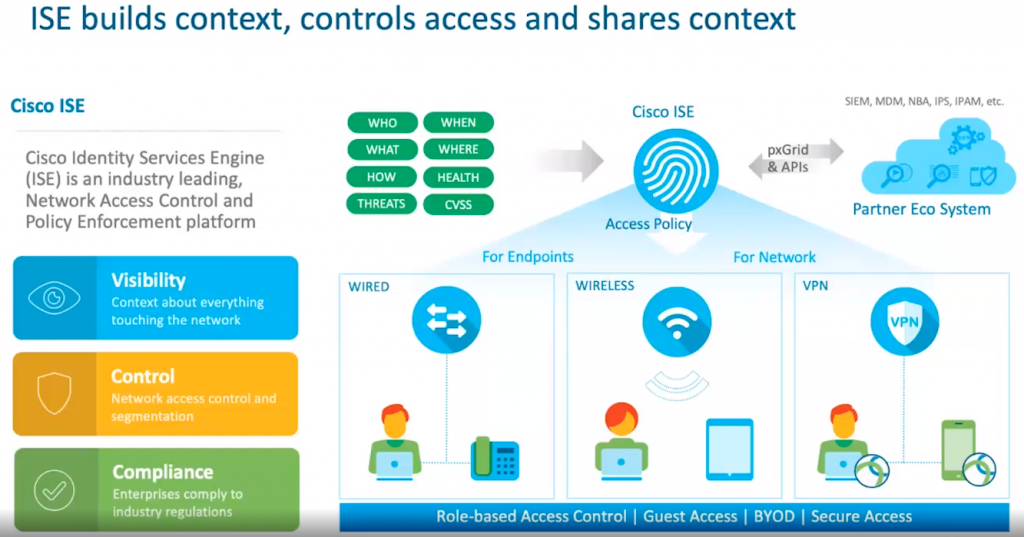
What ISE can do ?
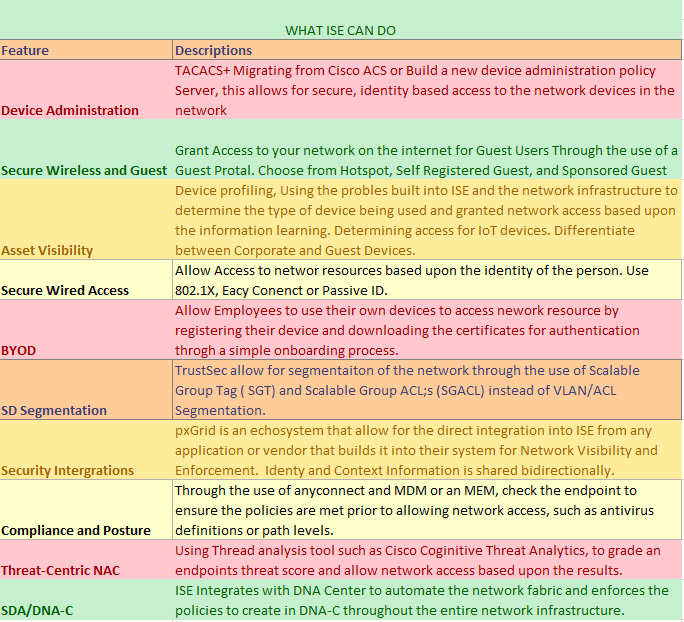
High level Solution Overview
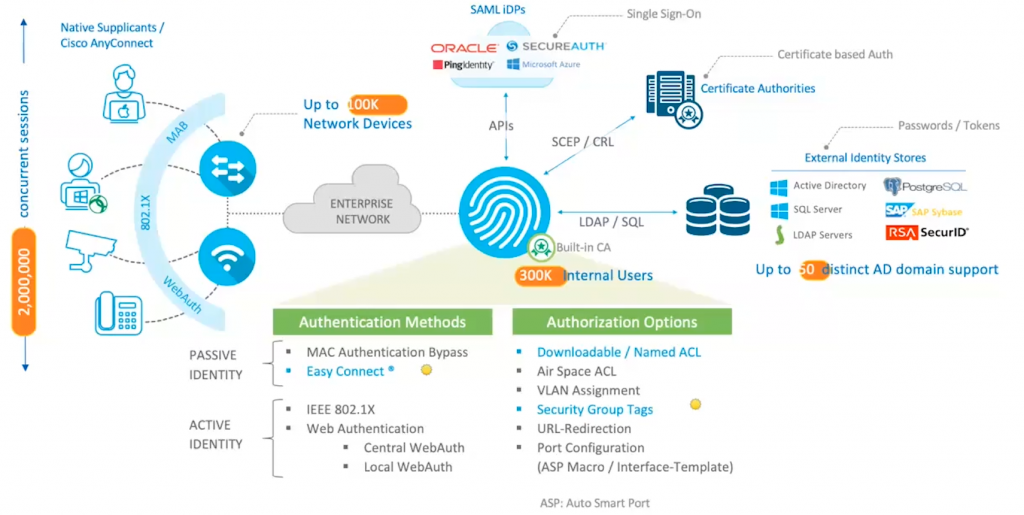
Selecting the RIGHT Model of the ISE device for your deployment.
Note : Make sure you spend some time on this and decide what model your required for your environment.
*Personally stay away from VM, – this will not give you as expected results, until you are dedicate resouces and Lock CPU – but it will be shared in esxi – never seen ISE or FMC Performs as expected like appliance Cisco build – DO NOT WASTE TIME think of VM.
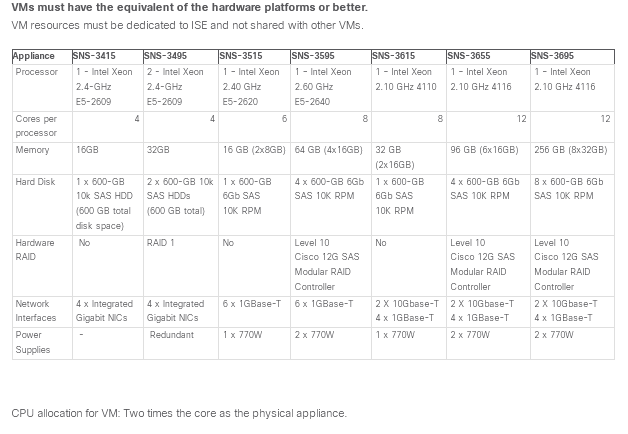
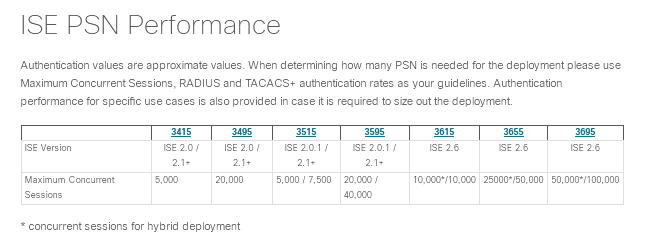
Hardware Performance PSN
How ISE can Adapt to Enviroment – From Scratch.
ISE required good planning – not like build the node it done miracles as expected.
I follow most experience steps – Once ISE Build and integrated with your environment. Start with
- Device Admin – which replaces your ACS with ISE for Role based access for the Devices in the network.
- Guest and Secure Wireless Access – this will secure your Guest users and your Corporate Wireless access.
- Asset Visibility – this will give you clear picture of environment what devices in the network and it will give you ability to make and plan – right VN ( DNAC ) – both macro and micro segmentation planning.
- Secured Wired Access – This will closed down your wired access with Dot1.X deployment – suggest to start with Low effected area to Critical area – not to do mass deployment.
- 4.1 – here you can introduce – Threat containment – for more securty visibility.
- BYOD – You can start planning – any non-authorised devices can get in to network and what kind of access can get back on the profiles.
- Segementation – this where your VN, Scalable Group come to play.
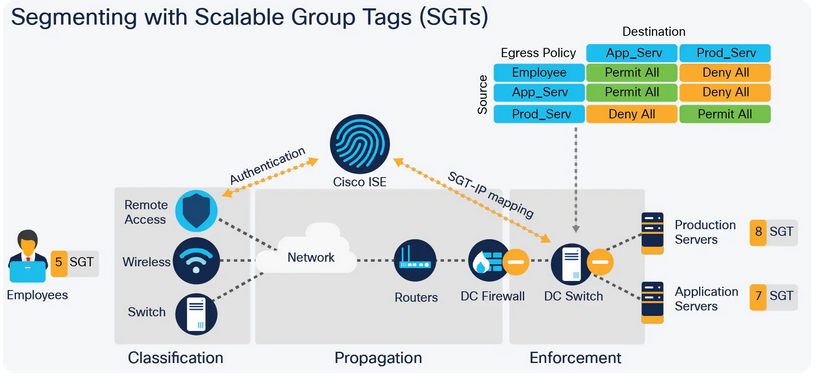
7. Security Echosystem integration – this more of pXGrid deployment with other partner systems.
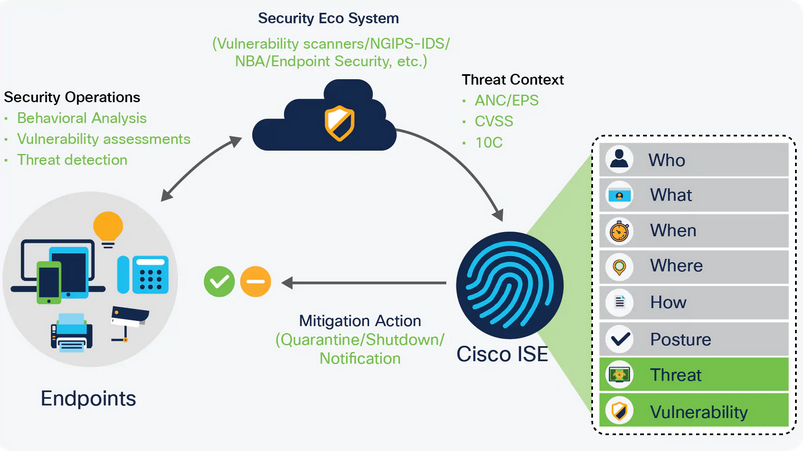
8.Complains & posture – for the Posture checks.
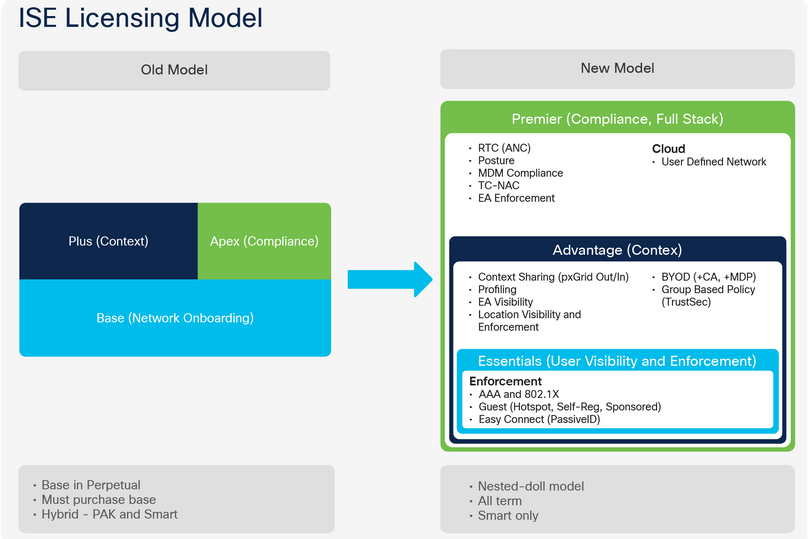
Since i have described how we can go gradually deployment – lets discuss also License requirement.
DNA Space with ISE
In the Desing level you can do all planning, what you can do as part of DNA center Design Level.
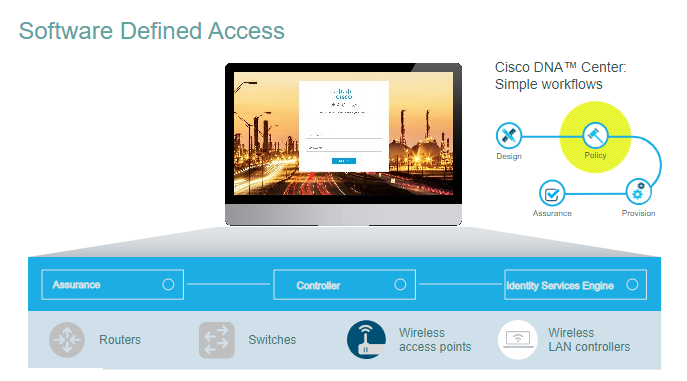
Elements required to make this happend, ISE Play Major role in SD-Access or DNAC space. this is part of the solution. you get 360 Degree visibility and take action in ~5sec (cisco claim ) to remidiate or block the attack going to happening in the network.
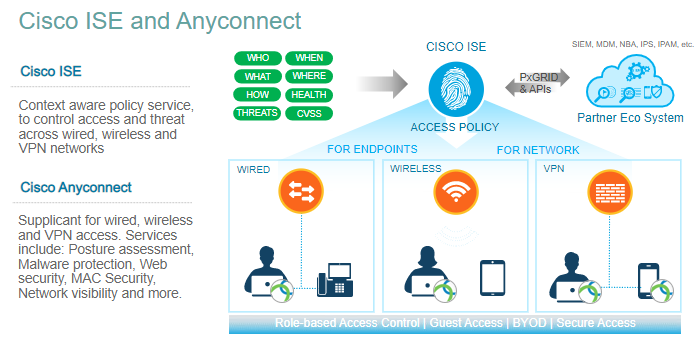
This is part of base design very clear matrix required what to access and what not.
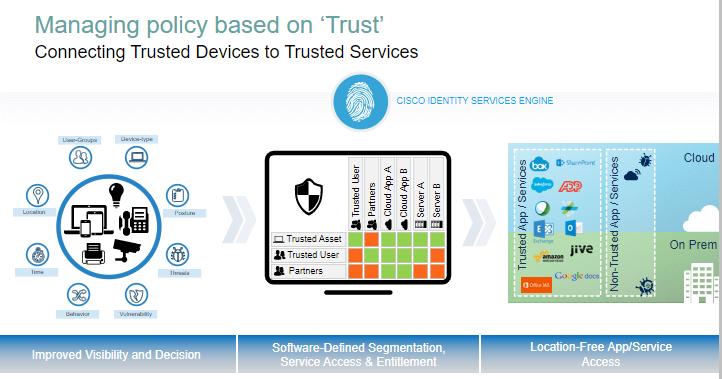
ISE Provide more visibility in the network.
I am running 2.4 as part of CCIE Sec requirement.

By Summary it shows –
Metric
- Total endpoints
- Active Endpoints
- BYOD Endpoints
- Compliance
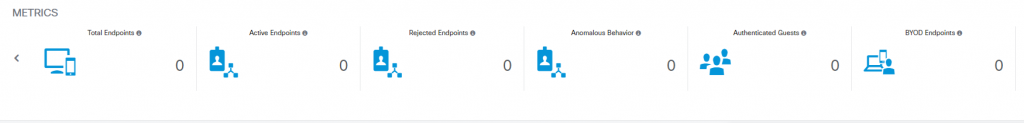
Authentications – by different device types and models
Network Devices – Switches, routers, WLC
Endpoints – end points
BYOD Endpoints – Guest non-trusted users
Alarms – this alarms and alerts. – user friendly readable.
System Summary – Overall system , status and cluster of ISE.
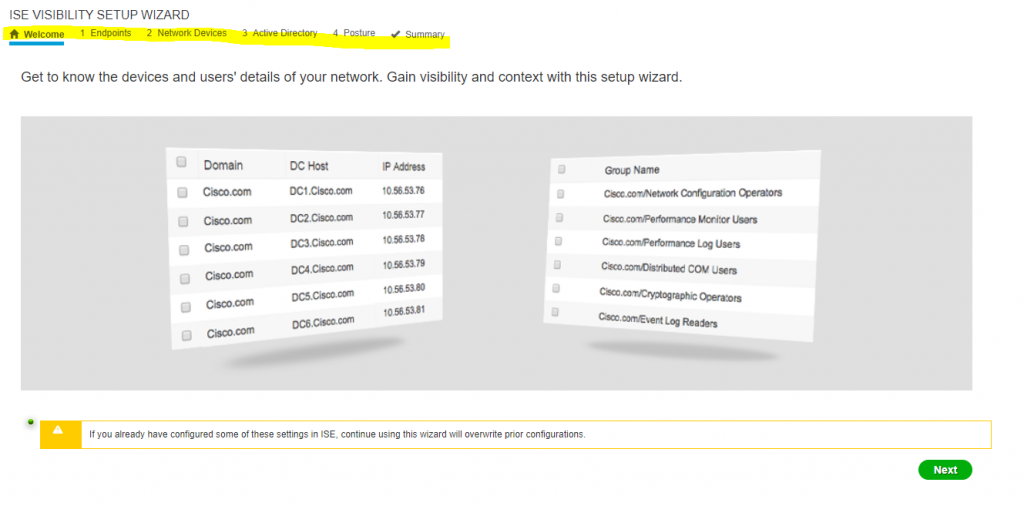
ISE – Visiblity Setup wizard
- it automatically finds and discovers it over all the network – and finds all devices with more information.
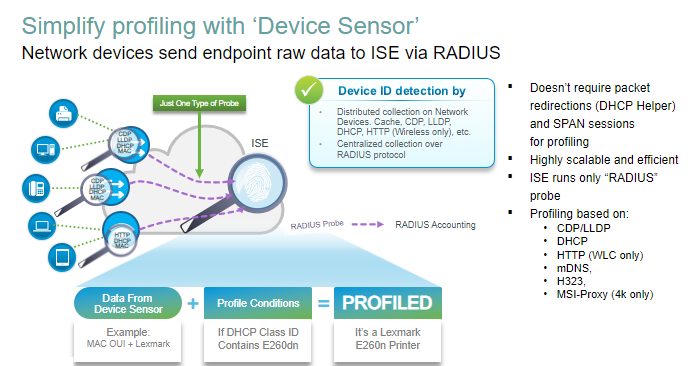
ISE Profiling work with ISE and DNAC
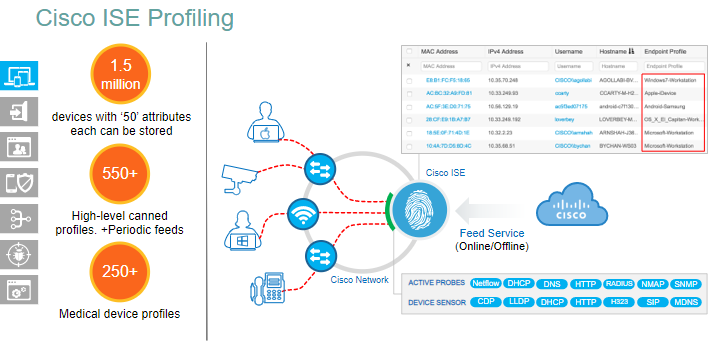
ISE does the Probing – 2 types Active and Passive
how the process works on high level.
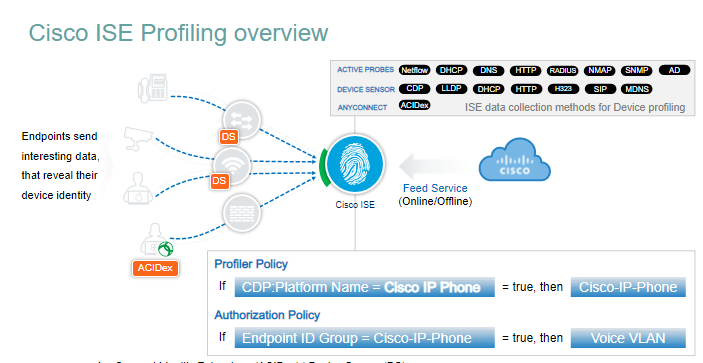
how the information collected based in Device Sensors
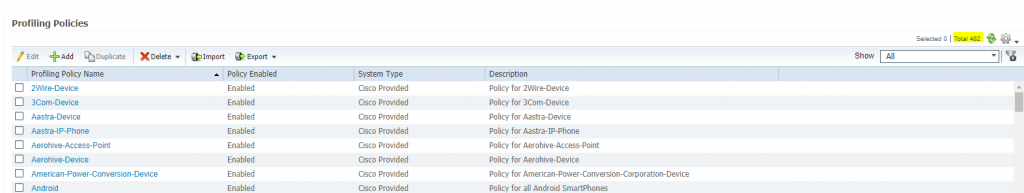
ISE come with defaul many profiles example :
More to add as it goes
Happy Labbbing !!!!