Cisco ASA: Site-to-site VPN between Cisco ASA & Cisco IOS Router
My way of journey learning Cisco Security : This article show you how to establish VPN between Cisco ASA and Cisco IOS router.
Some basics about VPN before i proceed to the config :
IKE Phase 1
In this phase, the firewalls use the parameters defined in the IKE Gateway configuration and the IKE Crypto profile to authenticate each other and set up a secure control channel. IKE Phase supports the use of preshared keys or digital certificates (which use public key infrastructure, PKI) for mutual authentication of the VPN peers. Preshared keys are a simple solution for securing smaller networks because they do not require the support of a PKI infrastructure. Digital certificates can be more convenient for larger networks or implementations that require stronger authentication security.
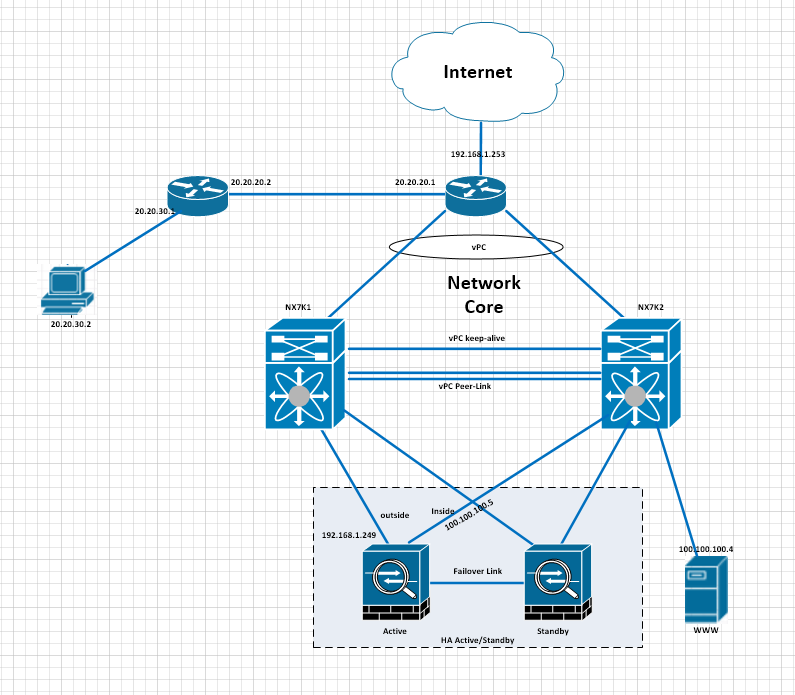
======================
1. Configure Interfaces
2. Configure ISAKMP policy
3. Configure transform-set
4. Configure ACL
5. Configure Tunnel group
6. Configure crypto map and attach to interface
7. Enable isakmp on interface
sysopt connection permit-vpn — Allow VPN traffic to bypass interface ACL
ASA Config :
============
1. Configure Interfaces
interface GigabitEthernet0/0
nameif outside
security-level 0
ip address 192.168.1.249 255.255.255.0
no shutdown
!
interface GigabitEthernet0/1
nameif inside
security-level 100
ip address 100.100.100.1 255.255.255.0
no shutdown
2. Configure ISAKMP policy
crypto ikev1 policy 10
authentication pre-share
encryption aes-256
hash sha
group 5
lifetime 86400
3. Configure transform-set
crypto ipsec ikev1 transform-set ESP-AES256-SHA esp-aes-256 esp-sha-hmac
crypto ipsec df-bit clear-df outside
4. Configure ACL
access-list VPN_SITE extended permit ip 30.30.30.0 255.255.255.0 20.20.20.0 255.255.255.0
5. Configure Tunnel group
tunnel-group 10.10.10.1 type ipsec-l2l
tunnel-group 10.10.10.1 ipsec-attributes
ikev1 pre-shared-key cisco123
6. Configure crypto map and attach to interface
crypto map VPNMAP 10 match address VPN_SITE
crypto map VPNMAP 10 set ikev1 transform-set ESP-AES256-SHA
crypto map VPNMAP 10 set peer 10.10.10.1
crypto map VPNMAP 10 set reverse-route
crypto map VPNMAP 10 set lifetime seconds 28800
crypto map VPNMAP 10 set pfs group5
crypto map VPNMAP interface outside
7. Enable isakmp on interface
crypto ikev1 enable outside
===============
Router IOS config :
===================
1. Configure Interfaces
interface GigabitEthernet0/0
ip address 20.20.20.2 255.255.255.0
duplex full
speed auto
media-type rj45
no shut
!
interface GigabitEthernet0/1
ip address 20.20.30.1 255.255.255.0
duplex auto
speed auto
media-type rj45
no shut
2. Configure ISAKMP policy
crypto isakmp policy 10
authentication pre-share
encryption aes 256
hash sha
group 5
lifetime 86400
3. Configure transform-set
crypto ipsec transform-set ESP-AES256-SHA esp-aes 256 esp-sha-hmac
crypto ipsec df-bit clear
4. Configure ACL
ip access-list extended VPN_HQ
permit ip 20.20.20.0 0.0.0.255 30.30.30.0 0.0.0.255
5. Configure Tunnel group
crypto isakmp key cisco123 address 10.10.10.2 no-xauth
crypto isakmp keepalive 10 3
6. Configure crypto map
crypto map VPNMAP 10 ipsec-isakmp
match address VPN_HQ
reverse-route
qos pre-classify
set peer 10.10.10.2
set security-association lifetime seconds 28800
set transform-set ESP-AES256-SHA
set pfs group5
7. Enable isakmp on interface
interface g0/0
crypto map VPNMAP
If all Good, you see the below Verification :
BRA2#show crypto isakmp sa
IPv4 Crypto ISAKMP SA
dst src state conn-id status
IPv6 Crypto ISAKMP SA
BRA2#
BRA2#
BRA2#show crypto isakmp sa
IPv4 Crypto ISAKMP SA
dst src state conn-id status
20.20.20.2 192.168.1.249 QM_IDLE 1001 ACTIVE
IPv6 Crypto ISAKMP SA
BRA2#show crypto ipse
BRA2#show crypto ipsec sa
BRA2#show crypto ipsec sa
interface: GigabitEthernet0/0
Crypto map tag: VPNMAP, local addr 20.20.20.2
protected vrf: (none)
local ident (addr/mask/prot/port): (20.20.30.0/255.255.255.0/0/0)
remote ident (addr/mask/prot/port): (100.100.100.0/255.255.255.0/0/0)
current_peer 192.168.1.249 port 500
PERMIT, flags={origin_is_acl,}
#pkts encaps: 30, #pkts encrypt: 30, #pkts digest: 30
#pkts decaps: 30, #pkts decrypt: 30, #pkts verify: 30
#pkts compressed: 0, #pkts decompressed: 0
#pkts not compressed: 0, #pkts compr. failed: 0
#pkts not decompressed: 0, #pkts decompress failed: 0
#send errors 0, #recv errors 0
local crypto endpt.: 20.20.20.2, remote crypto endpt.: 192.168.1.249
plaintext mtu 1438, path mtu 1500, ip mtu 1500, ip mtu idb GigabitEthernet0/0
current outbound spi: 0x35693C5C(896089180)
PFS (Y/N): Y, DH group: group5
inbound esp sas:
spi: 0x87CA1271(2278167153)
transform: esp-256-aes esp-sha-hmac ,
in use settings ={Tunnel, }
conn id: 1, flow_id: SW:1, sibling_flags 80000040, crypto map: VPNMAP
sa timing: remaining key lifetime (k/sec): (4358631/3579)
IV size: 16 bytes
replay detection support: Y
Status: ACTIVE(ACTIVE)
inbound ah sas:
inbound pcp sas:
outbound esp sas:
spi: 0x35693C5C(896089180)
transform: esp-256-aes esp-sha-hmac ,
in use settings ={Tunnel, }
conn id: 2, flow_id: SW:2, sibling_flags 80000040, crypto map: VPNMAP
sa timing: remaining key lifetime (k/sec): (4358631/3579)
IV size: 16 bytes
replay detection support: Y
Status: ACTIVE(ACTIVE)
outbound ah sas:
outbound pcp sas:
ASA Side Verification :
ASAV1# show crypto isakmp sa
IKEv1 SAs:
Active SA: 1
Rekey SA: 0 (A tunnel will report 1 Active and 1 Rekey SA during rekey)
Total IKE SA: 1
1 IKE Peer: 20.20.20.2
Type : L2L Role : initiator
Rekey : no State : MM_ACTIVE
There are no IKEv2 SAs
ASAV1# show crypto ipsec sa
interface: outside
Crypto map tag: VPNMAP, seq num: 10, local addr: 192.168.1.249
access-list VPN_SITE extended permit ip 100.100.100.0 255.255.255.0 20.20.30.0 255.255.255.0
local ident (addr/mask/prot/port): (100.100.100.0/255.255.255.0/0/0)
remote ident (addr/mask/prot/port): (20.20.30.0/255.255.255.0/0/0)
current_peer: 20.20.20.2
#pkts encaps: 62, #pkts encrypt: 62, #pkts digest: 62
#pkts decaps: 62, #pkts decrypt: 62, #pkts verify: 62
#pkts compressed: 0, #pkts decompressed: 0
#pkts not compressed: 62, #pkts comp failed: 0, #pkts decomp failed: 0
#pre-frag successes: 0, #pre-frag failures: 0, #fragments created: 0
#PMTUs sent: 0, #PMTUs rcvd: 0, #decapsulated frgs needing reassembly: 0
#TFC rcvd: 0, #TFC sent: 0
#Valid ICMP Errors rcvd: 0, #Invalid ICMP Errors rcvd: 0
#send errors: 0, #recv errors: 0
local crypto endpt.: 192.168.1.249/0, remote crypto endpt.: 20.20.20.2/0
path mtu 1500, ipsec overhead 74(44), media mtu 1500
PMTU time remaining (sec): 0, DF policy: clear-df
ICMP error validation: disabled, TFC packets: disabled
current outbound spi: 87CA1271
current inbound spi : 35693C5C
inbound esp sas:
spi: 0x35693C5C (896089180)
transform: esp-aes-256 esp-sha-hmac no compression
in use settings ={L2L, Tunnel, PFS Group 5, IKEv1, }
slot: 0, conn_id: 4096, crypto-map: VPNMAP
sa timing: remaining key lifetime (kB/sec): (4373996/3562)
IV size: 16 bytes
replay detection support: Y
Anti replay bitmap:
0xFFFFFFFF 0xFFFFFFFF
outbound esp sas:
spi: 0x87CA1271 (2278167153)
transform: esp-aes-256 esp-sha-hmac no compression
in use settings ={L2L, Tunnel, PFS Group 5, IKEv1, }
slot: 0, conn_id: 4096, crypto-map: VPNMAP
sa timing: remaining key lifetime (kB/sec): (4373996/3562)
IV size: 16 bytes
replay detection support: Y
Anti replay bitmap:
0x00000000 0x00000001
IOS router side connected Windows PC :
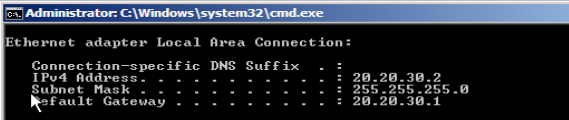
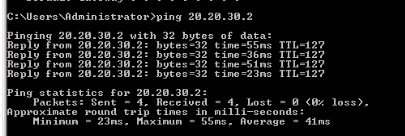
Pinging to other side Windows box.
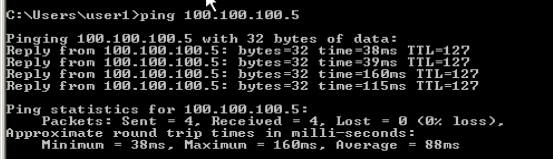
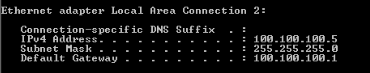
Pinging to other side Windows box.
DEBUGING :
========
debug crypto engine 127
debug crypto isakmp 127
debug crypto ipsesc 127
Phase 1 :
show isa sa
Phase 2:
show cry ipsec sa
CLEAR THE CONFIG IPSEC:
======================
clear config crypto
clear config group-policy
clear config tunnel-group
CLEAR THE CONFIG SSL:
======================
clear config webvpn
clear config group-policy
clear config tunnel-group