Smart License On Prem or Satellite Server.
If you registering device with Cisco smart License with cisco Cloud you do not have any issue – make sure your device can communicate to cisco on port 443
this document explain local SSM registration.
ip domain lookup source-interface Loopback0 <<- what interface you use to communicate to network)
ip http client source-interface Loopback0
ip name-server x.x.x.x (your local DNS)
crypto pki trustpoint LicRoot
enrollment terminal
revocation-check none
crypto pki authenticate LicRoot
<<>>
call-home
profile “CiscoTAC-1”
active
destination transport-method http
no destination transport-method email
destination address http https://LOCALDOMAIN.COM/Transportgateway/services/DeviceRequestHandler
!exit config mode
license smart register idtoken (generate a token form SSM website and add it to this command)
Cisco ca cer
—–BEGIN CERTIFICATE—–
XXXXXXXXXXXXXXX
XXXXXXXXX
—–END CERTIFICATE—–
If the Switch registration fails – things to check:
- Check any Root Certificate other than below – remove it
Below certificate to register SSM
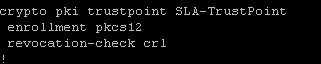
Config t
!
No crypto pki trustpoint SLA-TrustPoint
!
End
Wr
ping localserver.com from switch.
Happy Labbing..!!!