CML 2.8 Installation
Nov 2024 Cisco has released a new CML 2.8 version containing more advanced features and image addresses like SD-WAN and FTD/FMC. To learn my Cisco CCIE SEC Lab also has Cisco 9000v, with that you can test some of the features with ISE for 802.1x and other additional features required for the CCIE SEC Lab 6.1
Download from Cisco side below images :
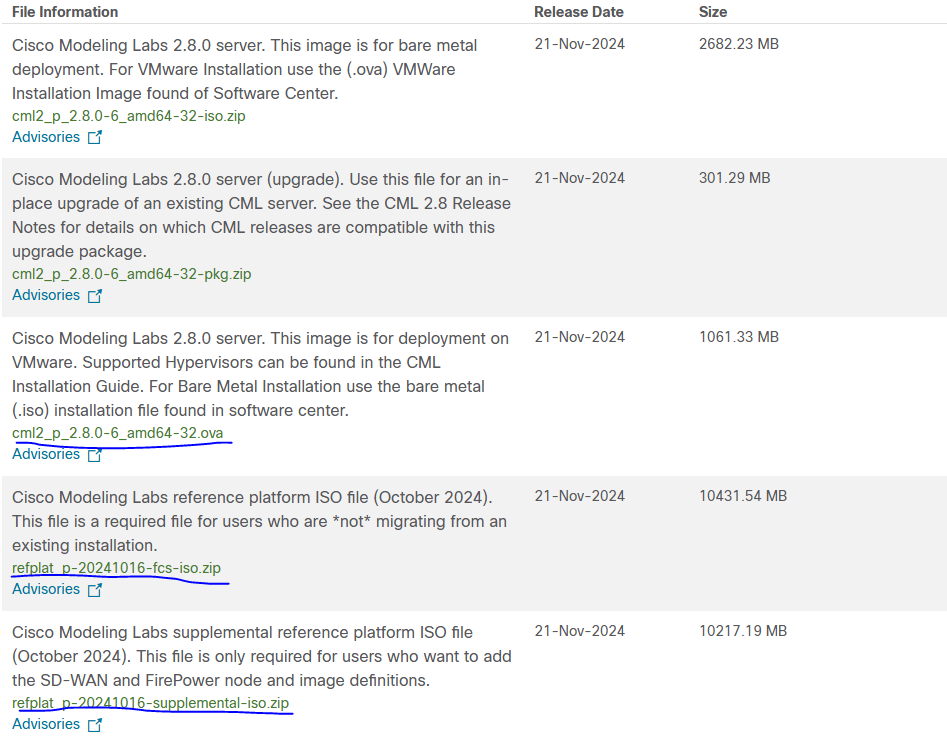
I am installing on Esxi 8.0 with 32 CPU and 128GB RAM, 3 TB SSD to start to explore the Labs.
Esxi starts a New Provision VM. Give it a name and Upload the OVA image previously downloaded from the Cisco side (uncheck the box to not start; I would like to change the additional compute required for the CML to use for more advanced Labs).
Edit CML VM on Esxi added below my requirement and save and start the VM.
You can start and continue the setup.

Accept the EUAL and continue; make sure you note the below ports for Adminstrate CML 2.8
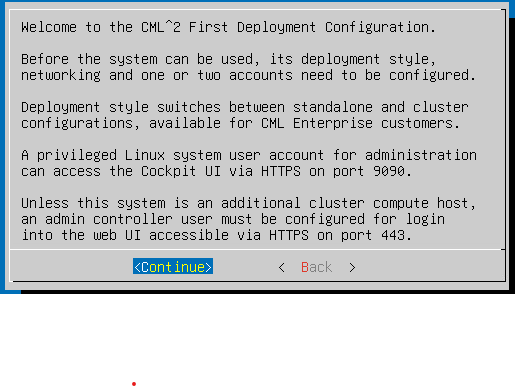
If you are setting up a Cluster, you need 2 Interfaces of NIC. I am running standalone, so 1 NIC is good to start the installation.
Give the name :
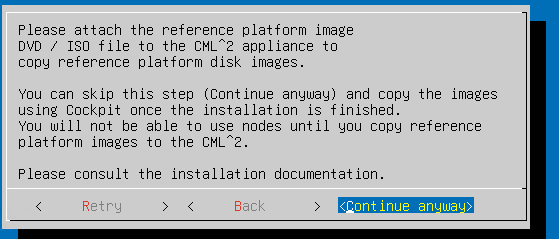
You can copy the images later – click continue anyway
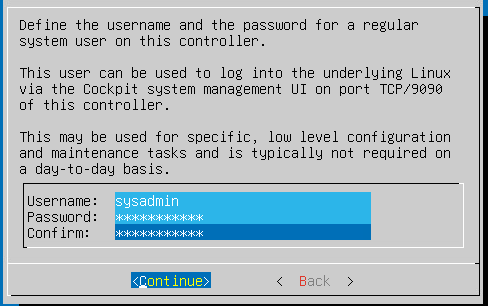
setup sysadmin password :
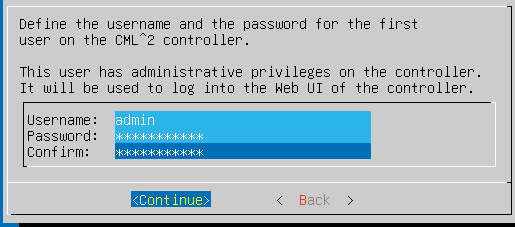
setup admin password :
I am using DHCP, so I have set up a DHCP. If you have static, select itbased on the requirement.
Click confirm to proceed for the installation
Now CML is installed we can use https access to login to CML 28
You will see a login prompt to see if all installations are working as expected. (no errors found)
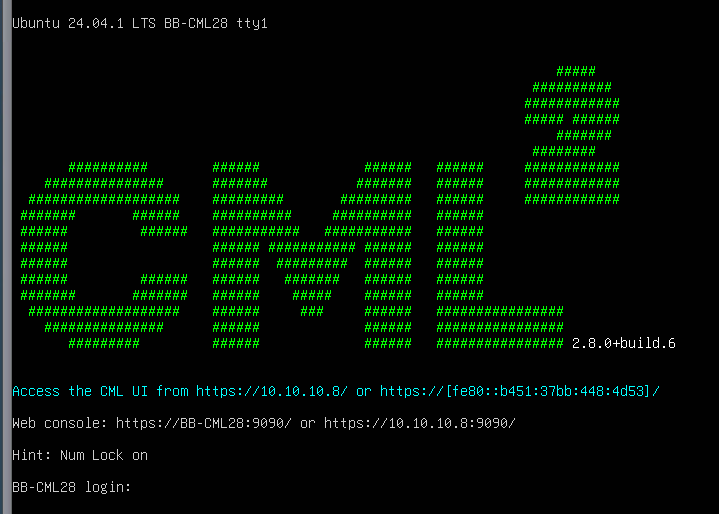
Now Installation is completed lets configure and understand the cockpit configuration
https://CML-28:9090 – for the cockpit URL for Login (CML-28 is your FQDN or IP address)
You log in with sysadmin/password (you set up when you installed the CML 2.8 part of the initial configuration.
each menu have different configuration task (more informaiton you can find CML documentation)
In the initial setup i missed to add ISO images for the node images, so I will show here how you can add them here.
First stop the CML 2.8 VM, extract
refplat-20241016-fcs.iso.zip and refplat-20241016-supplemental.iso.zip and upload to the ESXi Storage so you can use as ISO in CML 2.8 VM
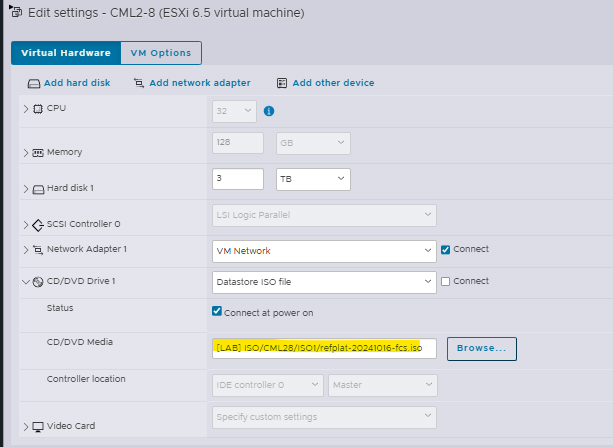
Power On the VM
Login to Cockpit https://cml-28:9090
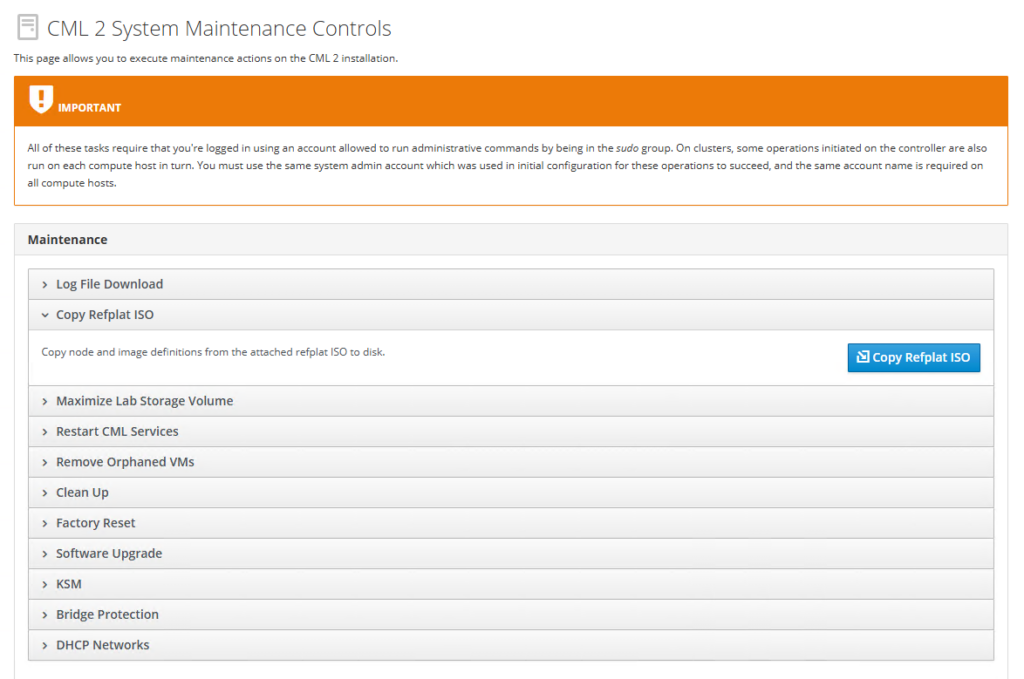
Make sure all the Labs are stopped before copying the images.
Click Copy Refplat ISO—it automatically copies from ISO 76 Images and one additional 28 images from supplemental ISO.
The CML Service will automatically restart part of the Copy files.
Now CML 2.8 ready for Labbing.
Lets Logging CML GUI to Create a Labs and testing
https://CML-28
Now good to start the New Labs (Make sure apply the right License for the Labs to use as expected).
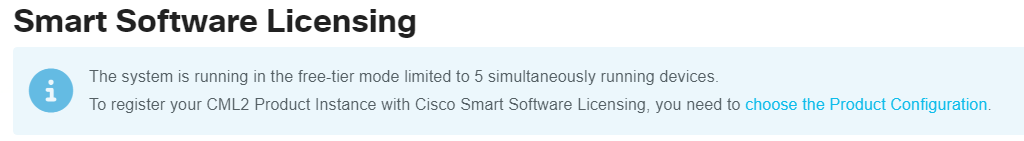
Good News on the new Version 2.8 5 devices free (but that is not as I expect for good lab testing) – but this gives look and feel of CML 2.8.
I have a personal License that can support up to 20 Nodes. This license allows me to do the testing for my CCIE Sec v6.1 testing.
Click the Choose the Product Confiuration.
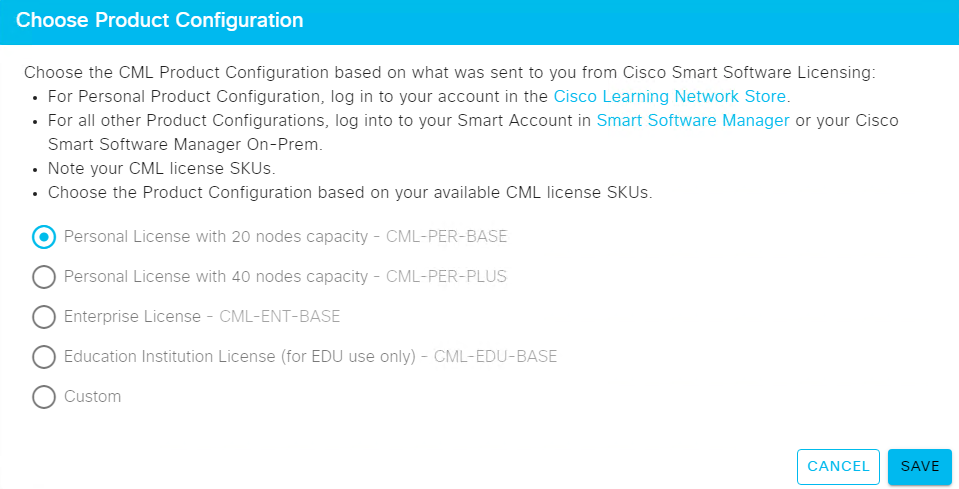
Click save
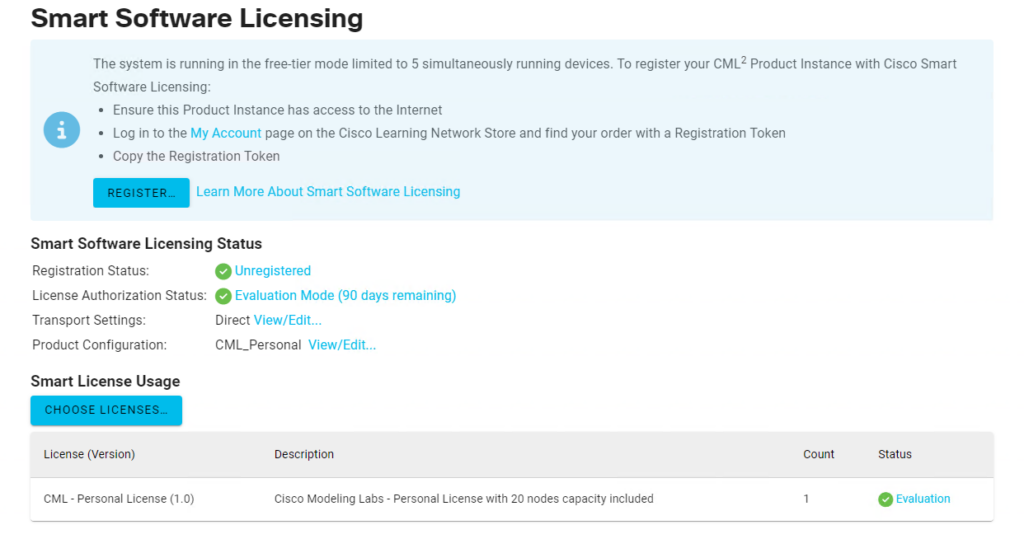
Click register with key to input
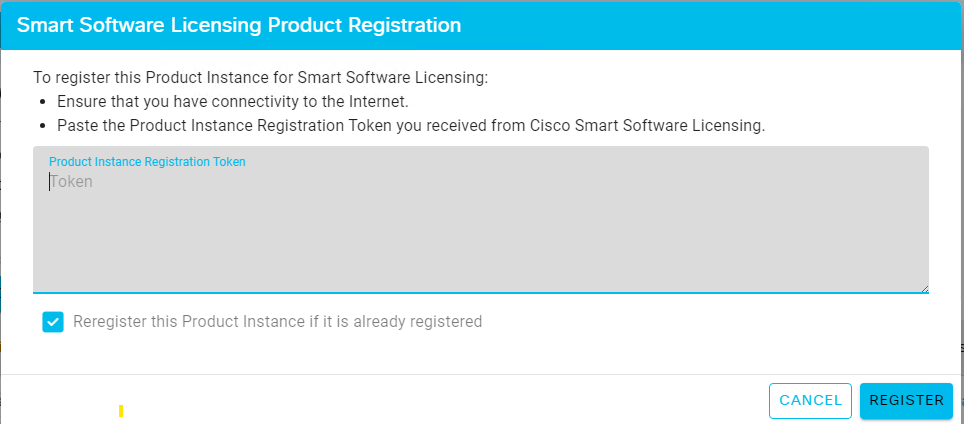
Enter the pre-register key and register
Happy Labbinggggggggggggggg !
I will post more CCIE SEC v6.1 Labs soon using CML.